Integrated Cloud Native Security Platform That Helps you Think like an Attacker
Invinsense Cloud Security Resources
Invinsense Cloud Environment
Cloud adoption is the fastest way to achieve digital transformation. The infrastructure, applications and platforms that took years or months, can now be built in weeks and days.
Cloud adoption is the fastest way to achieve digital transformation.
This speed has added to the vulnerability of already complex cloud environment. Adversaries have learnt the cloud environment faster and changed their techniques to launch cloud centric cyberattacks. Due to the complexity of cloud environment and architecture, businesses are yet to understand the security of this complex environment.
The infrastructure, applications and platforms that took years or months, can now be built in weeks and days. This speed has added to the vulnerability of already complex cloud environment. Adversaries have learnt the cloud environment faster and changed their techniques to launch cloud centric cyberattacks. Due to the complexity of cloud environment and architecture, businesses are yet to understand the security of this complex environment.
Hence in this cyberwar against adversaries, security professionals are lagging behind especially in the cloud environment.
Invinsense Services
INVINSENSE
Cloud
Invinsense Cloud is an
Integrated Cloud Native
Security Platform
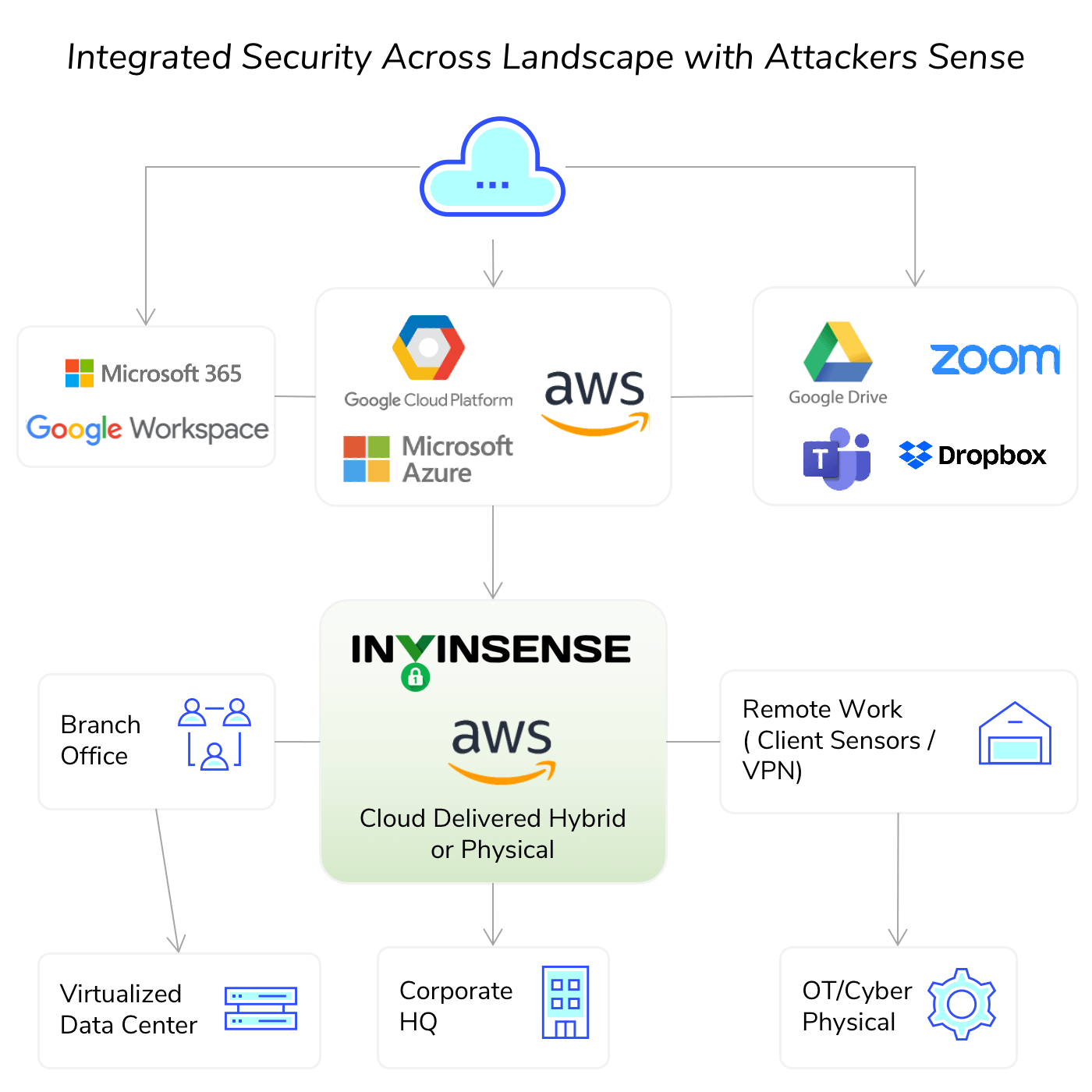
Invinsense Cloud is an Integrated Cloud Native Security Platform that gives visibility of various cloud components. It secures various modern cloud application methods like Monolithic, Container and Serverless. Invinsense Cloud has integrated AWS ready SIEM, SOAR, Deception, EDR and Offensive security tools.
Cyberattacks are coordinated and often a combination of manual and human intervention, Invinsense cloud is designed on the similar lines which combines cybersecurity strategy, solutions and services with understanding of attacker sense in the cloud environment. Our Cloud SOC services add the necessary human element to your cloud security posture. SOC for traditional security is different from SOC of cloud security that we provide. Invinsense Cloud adopts and provides security according to the need of various cloud application methods. It takes care of operating system and application security in the case of Monolithic, it takes care of application security and container security in the case of Container and it takes care of application security in the case of Serverless.
Invinsense Services
INVINSENSE
Cloud

Integrated Cloud Native
Security Platform
Invinsense Cloud is an Integrated Cloud Native Security Platform that gives visibility of various cloud components. It secures various modern cloud application methods like Monolithic, Container and Serverless. Invinsense Cloud has integrated AWS ready SIEM, SOAR, Deception, EDR and Offensive security tools....
Cyberattacks are coordinated and often a combination of manual and human intervention, Invinsense cloud is designed on the similar lines which combines cybersecurity strategy, solutions and services with understanding of attacker sense in the cloud environment. Our Cloud SOC services add the necessary human element to your cloud security posture. SOC for traditional security is different from SOC of cloud security that we provide. Invinsense Cloud adopts and provides security according to the need of various cloud application methods. It takes care of operating system and application security in the case of Monolithic, it takes care of application security and container security in the case of Container and it takes care of application security in the case of Serverless.
Read moreInvinsense Services
INVINSENSE
OODA
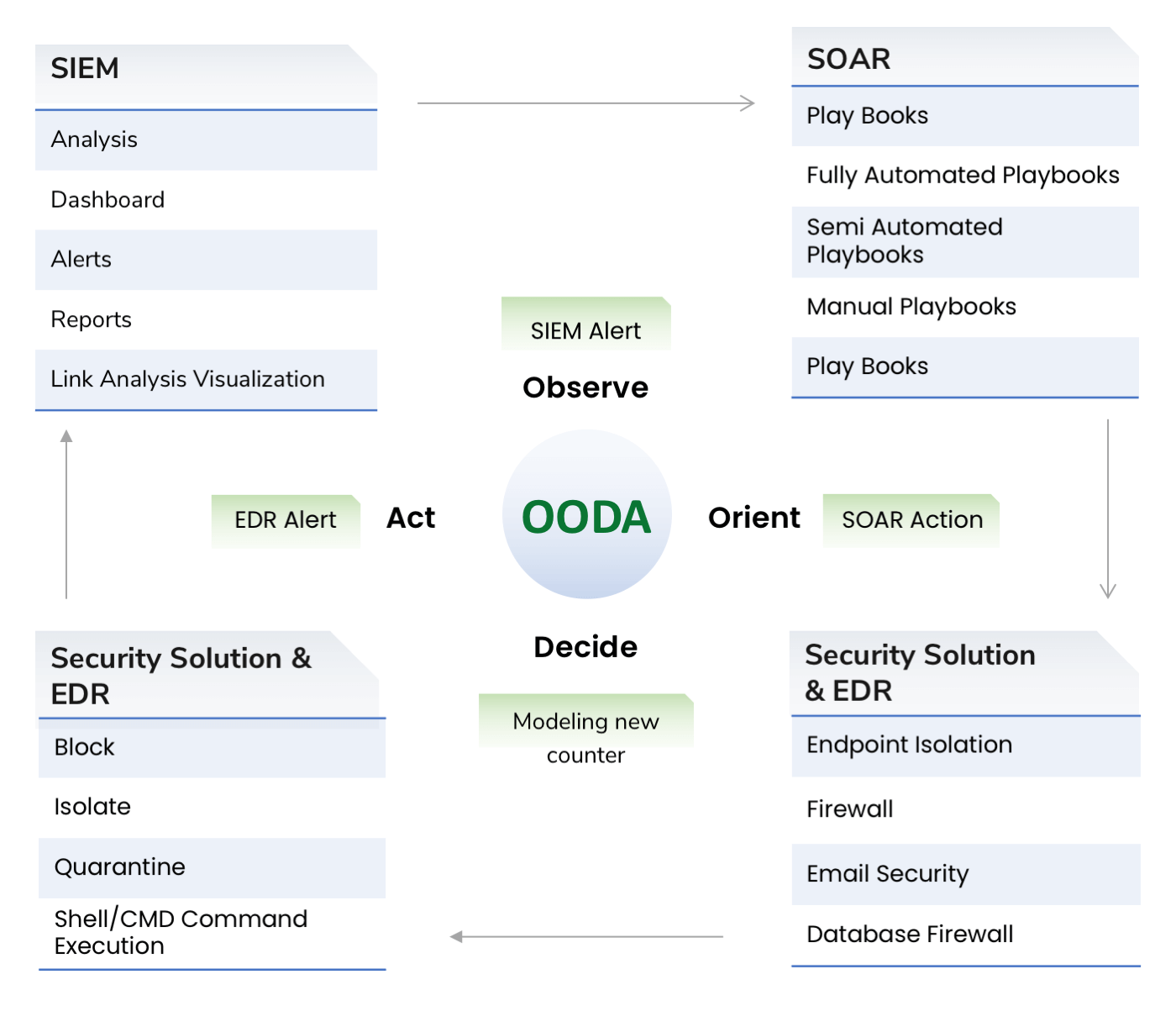
Threats to AWS and hybrid cloud environment are coordinated and work as a system
To combat them, businesses need not only need to have SIEM, SOAR, EDR and security solutions in their cloud environment, but they also need integration and coordination among these solutions to Observe, Orient, Detect and Act on the threats and neutralize them.
Invinsense OODA helps businesses to protect their cloud environment by providing integration of their security solutions and provide real time sharing of threat intelligence to provide cloud enabled and for cloud Security Operations Centre.
Invinsense Services
INVINSENSE
OODA

Threats to AWS and hybrid cloud environment are coordinated and work as a system
To combat them, businesses need not only need to have SIEM, SOAR, EDR and security solutions in their cloud environment, but they also need integration and coordination among these solutions to Observe, Orient, Detect and Act on the threats and neutralize them.
Invinsense OODA helps businesses to protect their cloud environment by providing integration of their security solutions and provide real time sharing of threat intelligence to provide cloud enabled and for cloud Security Operations Centre.
Invinsense Services
INVINSENSE
Deception of Cloud
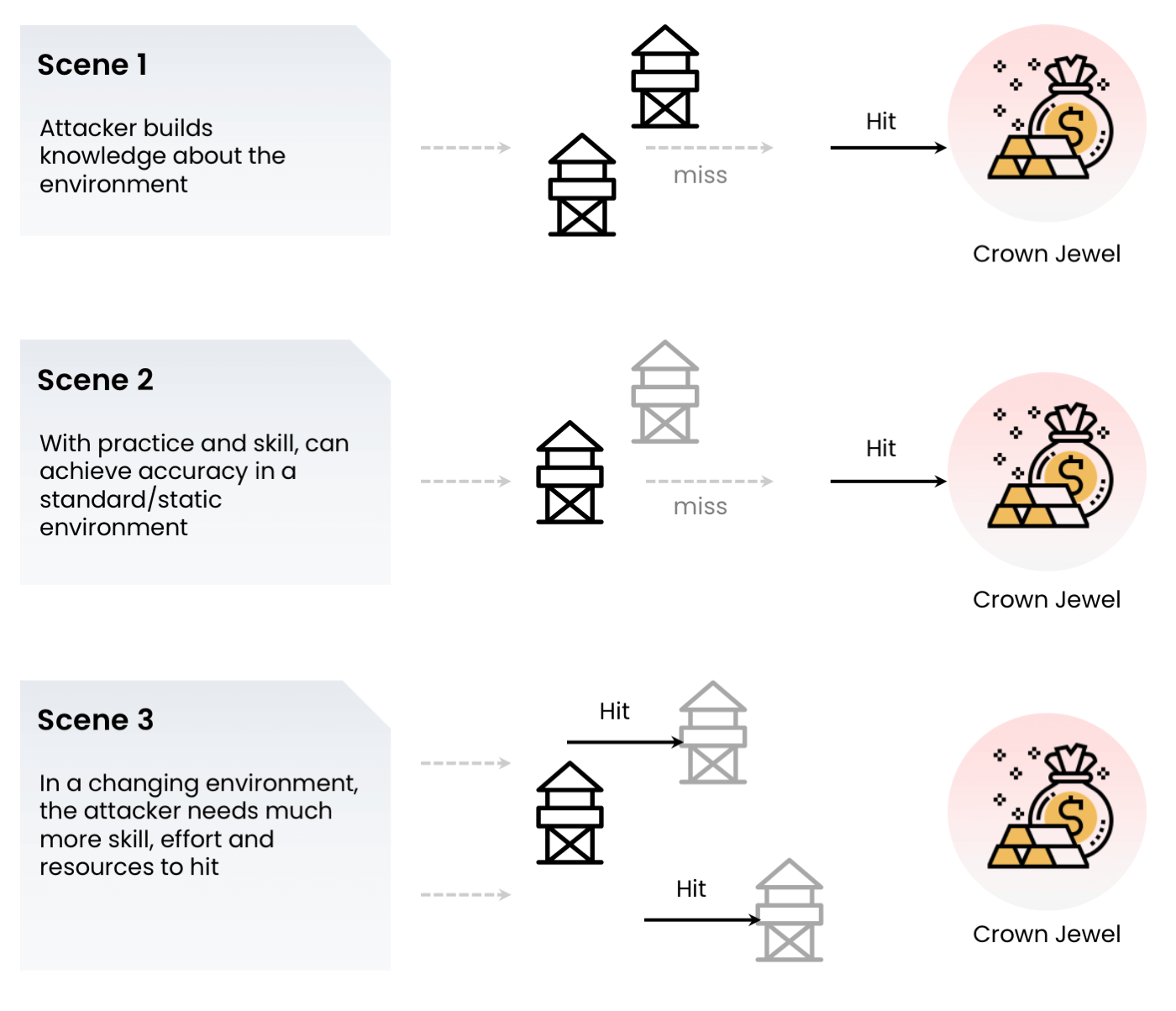
Cloud environment is complex and dynamic
On one side it has given so much of digital empowerment to organizations of all sizes and on another side it has also made many things vulnerable. Misconfigurations, open ports, clicking wrong things, etc ar e day to day small accidents that make cloud environment open for adversaries.
How to secure and protect one's crown jewel on cloud infrastructure is a growing concern. One thing is sure, adversaries are going to enter your cloud environment someday and cybersecurity on cloud needs to be prepared for that day. The best way to minimize the damage is we the use of Deception Technologies to protect cloud environment.
Deception helps organizations to dominate adversaries in the direction organizations want them to go, once they make their unwanted entry in to the system. Invinsense Cloud can easily set up a fake S3 Bucket or a fake IAM key or fake services or fake containers and even set up a fake EC2 instance in no time.
Once these are set up, it will surely lure adversaries towards these decoys set up in the environment. Once these fake lures are set up, it is easy to configure the log monitoring and alert feeds and integrate it with the SOC monitoring process. Once the attackers hit any of these decoys, these decoys can easily be isolated and the incident management process is completed.
This completely eliminates the false positives in the monitoring process. Invinsense cloud provides tight integration of Deception with Incident Detection and Response thereby providing a very effective Cyber Defense practice within the Cloud Environment.
Invinsense Services
INVINSENSE
Deception of Cloud

Cloud environment is complex and dynamic
On one side it has given so much of digital empowerment to organizations of all sizes and on another side it has also made many things vulnerable. Misconfigurations, open ports, clicking wrong things, etc are day to day small accidents that make cloud environment open for adversaries.
...How to secure and protect one's crown jewel on cloud infrastructure is a growing concern. One thing is sure, adversaries are going to enter your cloud environment someday and cybersecurity on cloud needs to be prepared for that day. The best way to minimize the damage is we the use of Deception Technologies to protect cloud environment.
Deception helps organizations to dominate adversaries in the direction organizations want them to go, once they make their unwanted entry in to the system. Invinsense Cloud can easily set up a fake S3 Bucket or a fake IAM key or fake services or fake containers and even set up a fake EC2 instance in no time.
Once these are set up, it will surely lure adversaries towards these decoys set up in the environment. Once these fake lures are set up, it is easy to configure the log monitoring and alert feeds and integrate it with the SOC monitoring process. Once the attackers hit any of these decoys, these decoys can easily be isolated and the incident management process is completed.
This completely eliminates the false positives in the monitoring process. Invinsense cloud provides tight integration of Deception with Incident Detection and Response thereby providing a very effective Cyber Defense practice within the Cloud Environment.
Read moreInvinsense Services
INVINSENSE
RBAS
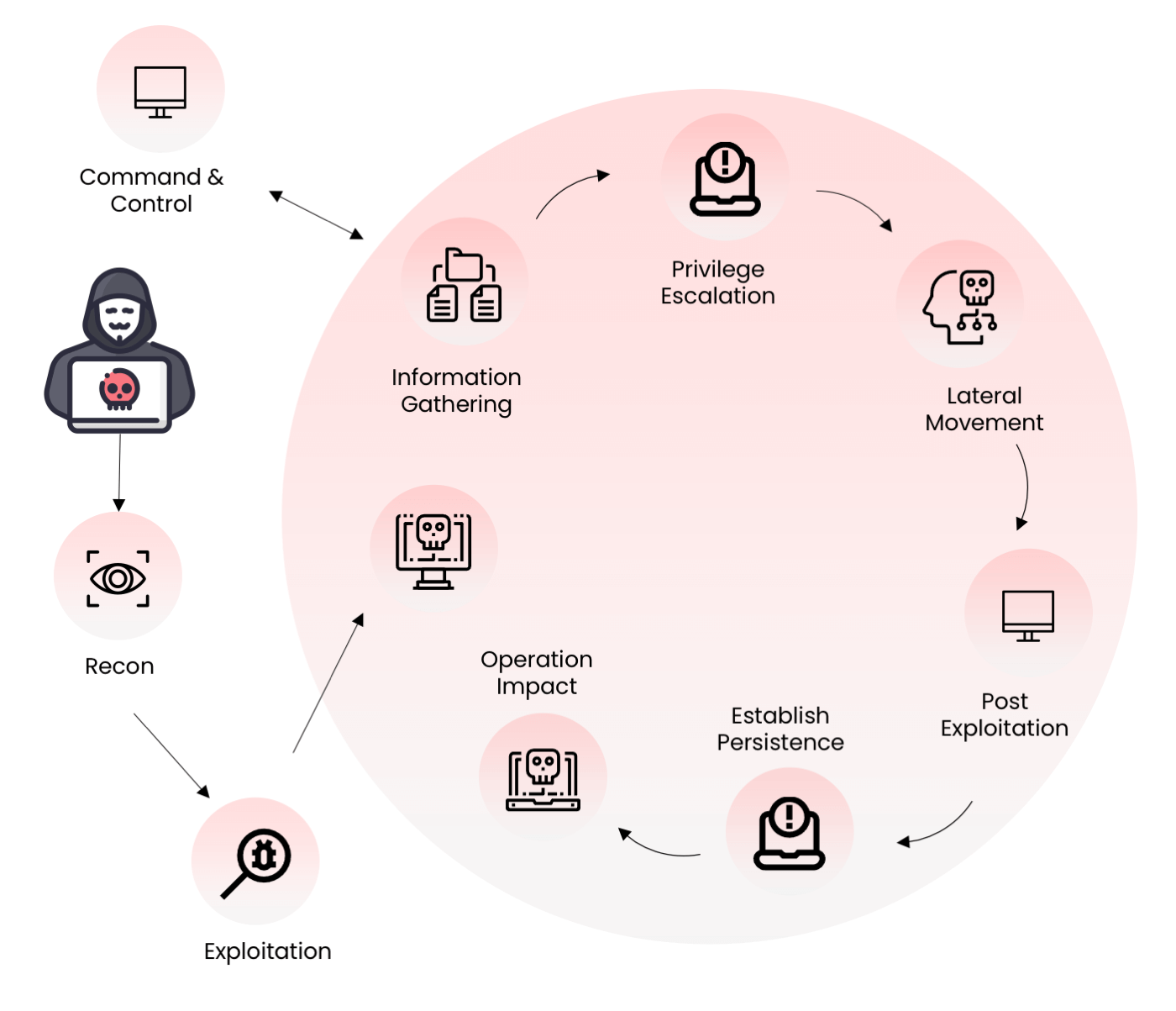
Cloud helps organizations to cover every weakness in their cloud security
The best way to anticipate vulnerabilities in the cloud environment and attacks that can follow is to actually simulate an attack capitalizing these vulnerabilities. Invinsense Cloud's Red Team and Breach Attack Simulation uses a combination of automation and human intervention to launch an attack and report the security posture of organizations in their cloud environment.
These reports expose every possible weakness in the cloud security posture and the tight integration with other solutions of Invinsense Cloud helps organizations to cover every weakness in their cloud security and attain a stable cloud security posture.