
On Monday, October 4, 2021, Apache published an advisory on CVE-2021-41773, Amazon CloudTrail is an excellent data source with a lot of API call history that allows us to keep track of who is attempting to do what in our AWS accounts.
But there is a little bit of problem with that too. We have a lot of call logging to analyze because every call is logged (including role assumption, role switching, and even the creation of a log stream).
According to a study, out of 400 million Cloud Trail Events, users just want only1 in 25,000 to be alerted of CloudTrail events. That’s an incredible signal-to-noise ratio!
Wazuh has a CDB List of AWS EventNames to reduce the signal-to-noise ratio and get the appropriate logs which needs to be monitored.
A CDB List (Constant Database) is a collection of values that are compared to a field extracted by a decoder. A custom rule checks whether the IP, user, or any other extracted information is present in the list from which we can determine whether or not to generate an alert based on the outcome.
Wazuh is a free, open source, enterprise-ready security monitoring technology that detects threats, monitors integrity, responds to incidents, and ensures compliance.
This feature’s primary purpose is to create a white/black list of users, file hashes, IP addresses, and domain names.
The list file is a simple text file with the following format for each line:
key1:value1
key2:value2
Each key must be unique, be preceded by a colon, and can contain an optional value. The value can be the others, but the key must be unique.
We can determine the existence or absence of a field in a list using a key. We can utilize a value as some rule criteria by adding it. For example, if we have account names (keys) that are linked to department names (values), we may create an alert that is triggered when a user who is not from the finance department connects into the finance server.
Wazuh has a default CDB list for AWS EventNames located in /var/ossec/etc/lists/amazon/aws-EventNames consisting of 346 EventNames by default.
There are some more AWS EventNames to be added of which logs are needed to be monitored:
For reference: There are more than 3000 EventNames which you can find on:
https://gist.github.com/pkazi/8b5a1374771f6efa5d55b92d8835718c
This list of AWS EventNames is to be added in /var/ossec/etc/lists/amazon/aws-EventNames.
For the new setting to take effect we need to restart the Wazuh manager.



We can see here, the changes from the additional list in the aws-EventNames file now reflects in the list.
With the help of this decoders and rules, we will get our events triggered and we will find it under the Security Events.
Login to your Invinsense Portal and open Wazuh
Here are the events which you can see in the Security Events for monitoring.
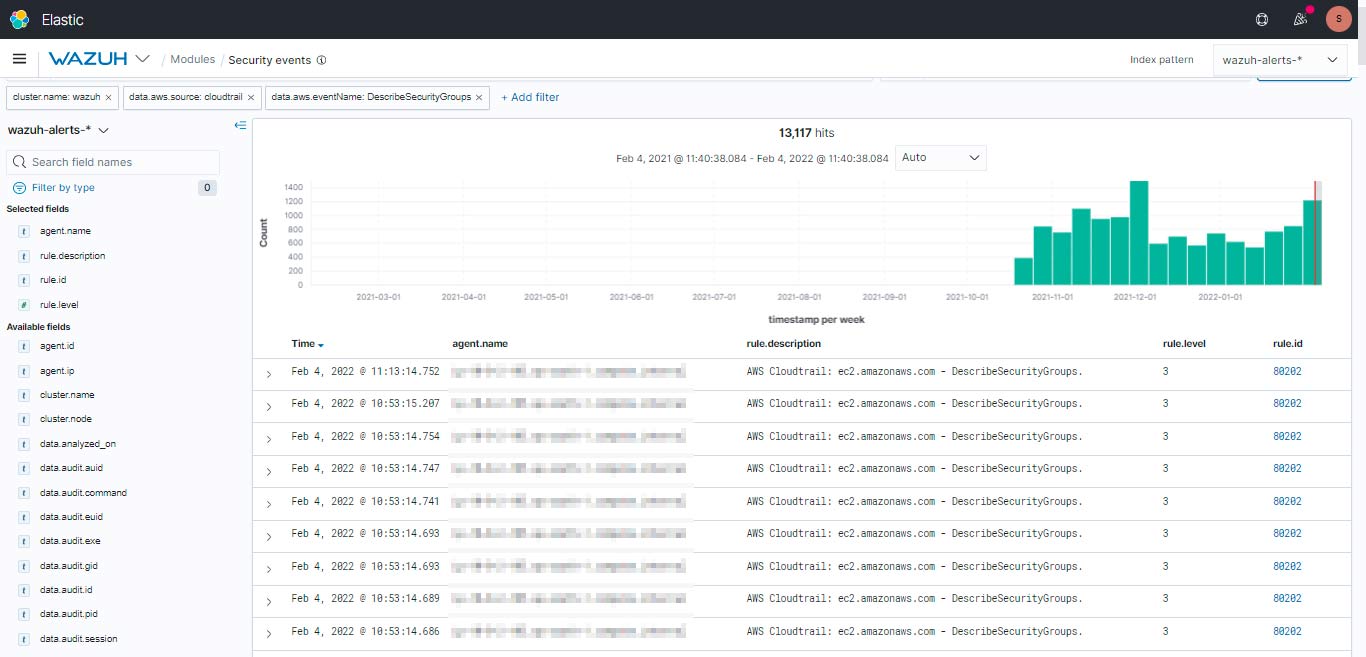
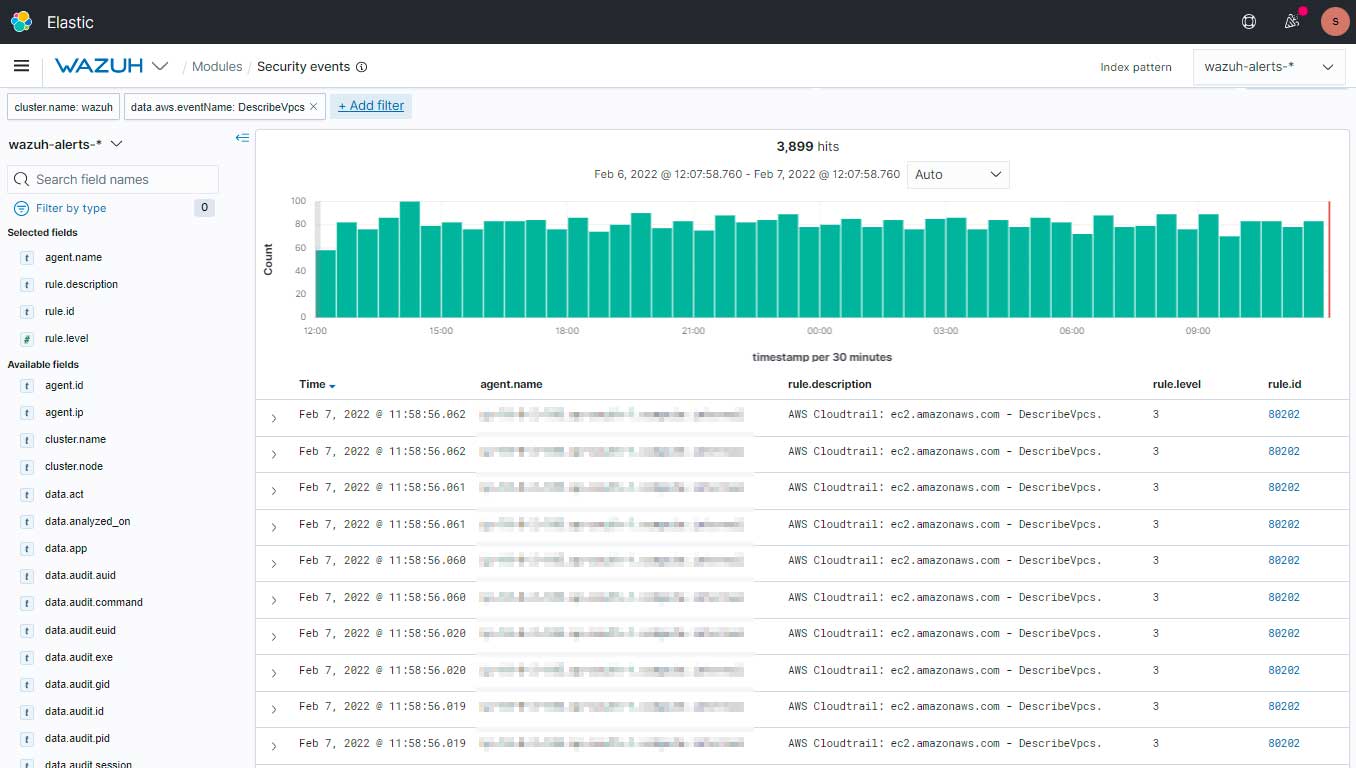
Using Wazuh and CloudTrail, we can reduce the signal-to-noise ratio and this is how we will get the AWS EventNames events in the security events and catch if any suspicious event that has occurred.
Discover complete cybersecurity expertise you can trust and prove you made the right choice!
