
Just recently, CDK Global paid a $25 million ransom in Bitcoin to stop the cyberattacks that crippled its operations and lasted for two weeks.
It was so bad that the company had to resort to using pen and paper to conduct its business.
This is just one of many examples, but when attacks like these happen, the standard process is that companies apologize and promise their customers to strengthen the security of their data, and then everything goes hush-hush until the next attack happens somewhere else.
Every organization’s standard line after the breach is: We take security very seriously.
But the vicious cycle of cyberattacks continues. In the end, where does the buck stop?
But something has to be done. A cyberattack damages both the revenue and reputation of an organization, threatening its survival.
That’s where you, a CISO, come into the scene.
The organization has tasked you with building a cybersecurity program that not only prevents cyberattacks but also keeps all its assets secure.
This comes with many challenges, as the odds are stacked against you.
Building a cybersecurity program is challenging.
This is evident from the fact that most companies don’t even have complete data on what assets they have within the premises.
Furthermore, these organizations strictly enforce the code of conduct and HR policies but ignore security policies.
They don’t hold their employees accountable for lapses in following all the security protocols.
To build a cybersecurity program for your company, you need to first face the fact that for organizations, security is not much of a priority since it doesn’t contribute to the bottom line.
Your first task will be to raise awareness among the company and take security seriously, which will require continuous efforts and patience.
Whether a company has awareness about cybersecurity or not can be determined based on how it responded after an attack.
If your answer to all this is yes, then your company really is well aware about cybersecurity. If not, then it lacks the cybersecurity culture.
Another reason why building a cybersecurity program is difficult is that nobody in your company understands the complexity of your job.
They don’t realize that you have to handle diverse tasks like providing:
This is quite a demanding job and is a harsh reality that every CISO has to face when building a cybersecurity program.
We are not trying to be pessimistic here or try to demoralize you with what we expressed in the previous section.
The situation we described in the previous section is the reality of most companies out there.
To build a cybersecurity program in this environment, you first need to give up on the mentality of having perfect and ideal security, which is not possible.
Perfection is a myth.
Rather, building a cybersecurity program is like running a marathon, where each lap you finish should bring you closer to your goal, which is to secure the data and systems of your organization.
So, focusing on making incremental progress that continually improves your company's cybersecurity posture is the best way to go.
Don’t try to achieve everything in one go.
Also, one of the major problems with the cybersecurity industry as a whole is its overreliance on tools to deal with threats.
This industry thrives on fear as we are constantly told to assume the worst, and the adversary is planning to launch an attack on us.
The vendors take advantage of this emotion to push the companies to adopt more cutting-edge tools.
The end result is that managing cybersecurity becomes an extremely complex task due to having too many tools with different functions. It creates a nuisance for everyone.
Our advice is that you don’t just create a strategy that revolves around the tools.
Rather, focus on the employees, too, since they will also play a valuable role in securing your organization.
We suggest that you go beyond tools and include people in your cybersecurity strategy so that they do their part in securing the assets of your organization. For this, you will need to build a strong relationship with them.
Let’s explore how you can do it in the next section.
As a CISO, you have to be like a statesman if you want to build a strong cybersecurity program in your organization.
What does a statesman do? They look after the interests of multiple groups to get their support and votes.
Similarly, you will need to prioritize and take care of the interests and goals of other departments to secure their cooperation.
If your cybersecurity program threatens their interests and goals, then it is bound to fail.
Many people working in the cybersecurity industry complain about the lack of cooperation and clash of egos with other departments.
For example, the security team has identified some areas of the organization where security can be improved.
But this requires the support of the system administrator who is not very open to making the changes, as they are perfectly comfortable with everything as it is, and starts to resist.
So, simple changes like enabling certain security features get escalated to the management since the system administrator is comfortable with the internal processes and doesn’t want to change them.
This frustrates the cybersecurity team.
Another problem that people in cybersecurity need to overcome is the false consensus effect.
This is a bias where we tend to overestimate how much other people agree with our own beliefs, behaviors, and attitudes. This is a human problem, not unique to cybersecurity.
But, as a CISO, you need to accept that not everyone sees security the way you do. Their views will be completely different from yours.
So, in such a situation, how can one build a rapport with other departments to get them to cooperate in securing the organization? Well, first of all, change how you present problems to them.
Cybersecurity is like detective work where you have to hunt for vulnerabilities, weaknesses, and security lapses and find the culprits behind them, which often ends up to be employees of other departments who are being too careless in their job, but don’t go around confronting them, that will only worsen the situation.
Abandon this mindset that it is you vs other departments. Rather, it is you and other departments who are against cybersecurity threats. You need to forge an alliance with other departments to deal with the common enemy, which are cybercriminals.
But to build this alliance, first stop with finger-pointing, which happens when you point out the poor security practices of employees working in the other department. This may feel humiliating to them, making them your enemies instead, which will ultimately benefit the cybercriminals in the end.
Criticism will always fail when presenting your findings to other departments.
So, how can a CISO tackle this problem? Through decentralization. Let other departments scan their systems and deal with the results as they see fit, whereas you and your team handle the vulnerability management. Although, in case there is a cyberattack, then do take charge of scanning their systems, but until then, let the individual departments have full control on how they manage their systems and its vulnerabilities. Although, do keep a bird's eye view on everything.
Keeping your organization’s assets secure, while maintaining harmony with other departments. That should be your goal.
Having strong relationships with other departments will also play a crucial role in building the fundamental structures of your cybersecurity program, which is the IT Policies and Procedures.
For IT policies and procedures, you need to create three documents that will act as the main structure of your cybersecurity program. These documents are:
The information security policy establishes a set of protocols that all employees must strictly follow to protect your organization’s systems and data. This document will act as a guide for the employees regarding the do’s and don'ts within the office premises.
But before you start working on this document, first determine the tolerance level of your organization. How much tolerance does your company have for breaches and information loss that occurs due to the attacks? What is the tipping point? How much is enough before the leadership that was previously uninterested in cybersecurity suddenly starts to take it seriously?
To determine this, take a look at attacks that happened to the organization in the past. That’s the best way to gauge how much appetite the company has for breaches and information loss.
In the aftermath of the attack, did the company allocate enough resources to boost the security of its systems? If so, then by how much?
Was anyone held accountable for the loss of data? If yes, then what kind of action did the organization take against them? Were they fired, or was it just a slap in the wrist?
Was the management notified of the attack? If yes, then how did they react? Was it in a casual way like “Yeah, we will look into it,” or was it a serious, all-hands-on-deck approach?
The answer to these questions will reveal the tolerance and standards your organization has for a data breach.
The next step is to come up with an information policy document that reflects the company’s risk tolerance level.
One mistake that many CISOs make is creating a document that reflects government or industry standards, but is totally divorced from the reality of the organization’s standards.
That’s where these policy documents fail to achieve their purpose.
Industry standards like ISO, NIST, or OWASP are geared towards watertight security with absolutely no tolerance for any risks.
This is not the same in your organization where the security standards are quite different and the risk tolerance is different.
The one size fits all here approach won’t work.
So, ensure that the information security policy is aligned with the security standards of your organization.
While your organization should strive to maintain standards that are stated by ISO, NIST, and OWASP. But as we said previously, cybersecurity is a marathon where you should focus on making incremental progress towards building a strong security posture instead of trying to achieve perfection at the get-go.
So before implementing the ISO, NIST, or OWASP standards, ensure that your organization reaches the awareness level where they want their cybersecurity to be guided by these frameworks. It’s better to let the company come to this conclusion on its own instead of brute forcing this change, which will only backfire in the end.
Once the first draft of the information security policy is created, share it with all the departments and get their feedback. This might take months since everyone is busy with their tasks and deadlines, so you will have to keep asking them like shameless salesmen to get feedback.
But this feedback is worth it, as the policy will be more closely aligned with the organization’s security standards.
Furthermore, the policy document should be reviewed every six months since the situation will never remain the same. What if the company faced a really bad cyberattack, and now the leadership wants tight security to safeguard its data and systems? The information security policy document needs to reflect the new reality.
If you have joined an organization where an information security policy document already exists, then avoid the temptation of changing it immediately. You will be seen as an outsider who is unnecessarily poking their business in company internal matters.
Wait for six months; until then, first understand the company’s culture and its people, and then make your move.
Having a cybersecurity charter is a great way to make the leadership and different departments care about the security aspects of the organization. This will solve one of the crucial problems that we have mentioned above, which is that people are indifferent to cybersecurity.
A cybersecurity charter lays down the roles and responsibilities that every department will have in maintaining the security of the organization.
Everyone will have a clear purpose for what they are supposed to do in keeping the organization secure. For example:
These are just a few examples, but keep the charter short and simple.
When other departments and the leadership are involved in the development of the charter, they will end up developing a stake in it.
By having a say in the charter, it is natural that they will take more interest in it. You can ask for their thoughts and ideas on what should go into the charter and get their feedback on the draft.
This is also a perfect opportunity to educate them about cybersecurity and influence their thoughts on it.
It will establish a better cohesion between cybersecurity and other departments, in which you get a perspective on what other departments think of cybersecurity, whereas they will get a better point of view on cybersecurity and your job. This exposes everyone to the challenges and struggles of each other, thus bringing them closer towards cooperation.
Share your draft with the leadership to get their writ on it, thus lending credibility to the charter. You can also use this as an opportunity to convince the CEO of your vision on how the cybersecurity program should be for the organization. Their support is crucial in bringing change within the organization.
In the end, a cybersecurity charter will ensure that an organization's security becomes a collective responsibility instead of just being your headache.
Nowadays, cyberattacks keep happening on a daily basis. So, it’s best to prepare your organization to deal with such attacks. That’s where a security incident response plan comes into play. This document comes in handy when an organization is facing a cyberattack.
During the attack, you and your team will be leading the company in overcoming the attack. All the spotlight will be on you as other departments will be counting on you to determine what went wrong in their systems, which will be revealed through log analysis. They will be more receptive to your suggestions and won’t mind your team accessing their systems. This is one of the best times to push for the changes that you wanted to bring for so long.
When preparing the document for a security incident response plan, take inputs from other system owners, as cybercriminals will target their systems during the attack.
Add a section for roles and responsibilities, a flowchart on how the cyber-attack should be handled, and what roles and responsibilities everyone will have during the breach.
Every incident you record should end with what lessons the organization has learned to prevent similar incidents in the future. There are great lessons in failure, provided one analyzes and learns from it.
The cybersecurity industry keeps pushing cutting-edge tools to provide different security services. This creates silos and unnecessarily complicates everything.
Invinsense rectifies this problem by bringing all security tools under one platform. Let’s take a look at them one by one.
Invinsense OXDR has put together different offensive security tools in one place to help your organization better predict and respond to future attacks.
Just as adversaries follow a four-phase methodology when attacking an organization, Invinsense OXDR also has a four-phase process to deal with the attacker at every level.
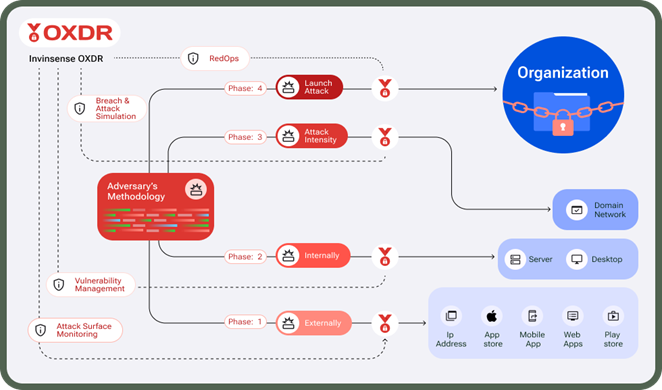
In phase 1, Invinsense OXDR will continuously monitor external access points like IP addresses, App Store, Mobile Apps, Web Apps, and Play Store.
This is because adversaries will often try to attack your organization through these access points. For example, they may create a duplicate application that your organization uses, upload it to the app store, and use it to dupe your employees.
In phase 2, Invinsense OXDR will perform a vulnerability assessment on your organization’s servers and desktops that employees use for their work to detect any weakness that the adversary can exploit.
In phase 3, Invinsense OXDR will simulate actual cyber-attacks (through tactics, techniques, and procedures used by adversaries) to test your organization’s security posture and see how well it will fare in the face of an actual attack.
In the final phase, Invinsense OXDR will launch an all-out attack (more intense than previous ones) using actual attacker techniques. This will reveal whether your organization is prepared enough to fend off an actual attack. This phase will also identify areas of improvement needed in your infrastructure.
As we mentioned previously, a CISO has to handle diverse tasks like providing risk assessment services, web Application pen-testing, red team exercises, incident response services, tabletop exercises for simulated incidents, and awareness training for all employees. Invinsense GSOS can help you with these tasks.
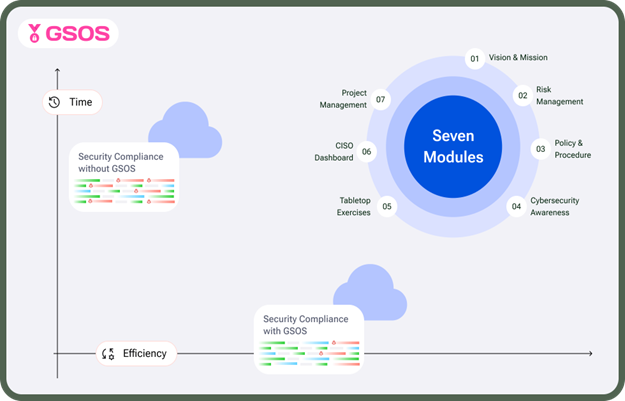
For example, let’s say you want to conduct tabletop exercises within your organization.
Invinsense GSOS has tabletop simulations in which you can hold different types of simulations to train your colleagues. There are 27 tabletop simulations to choose from when you are conducting awareness training for all employees in your organization.
Furthermore, Invinsense GSOS has a Compliance Documents Section where you can share the draft of your information security policy, cybersecurity charter, and security incident response for other departments to see and review. You can also store all your policy procedure documents here.
With the risk management section, your team will get an overall view of the organization’s cybersecurity posture. This will help you in prioritizing where to allocate resources to strengthen the security of your company. Also, your team will be able to assess vulnerabilities that exist in other departments, which you can then bring up with them.
Lastly, cyberattacks will keep getting more lethal in the coming future, which means more headache in dealing with the compliances that regulators will keep coming up with to deal with these attacks. Invinsense GSOS will help you deal with this headache by providing a dedicated team of experts to help you fulfill all the compliance requirements.
Additionally, our Project Management module will show you all the cybersecurity solutions running in your organization. It further gives insights like patch status, software update status, risk score, compliance, and vulnerability management. This will keep your security strong, and you will stay up-to-date with everything happening in the organization
With Invinsense XDR, organizations will no longer need different vendors to perform various code security processes (SAST, SCA, DAST, IAST, Source Code Review, Software Supply Chain Security, Secrets Management, and SBOM) as everything is now being done from one single platform.
This prevents siloing, due to which the application has much better security.
Secondly, many DevSecOps vendors only focus on finding issues but don’t do anything to rectify them.
Invinsense DevSecOps goes one step ahead by not only focusing on finding different types of vulnerabilities but also patching them out.
This ensures that the workflow and productivity of developers don't get disturbed because of security tools, as they don’t have to do anything since Invinsense is taking care of everything.
Developers can focus on their tasks while we handle all the security aspects of their applications.
Furthermore, Invinsense Vulnerability Management will bring all the vulnerabilities reported by the code security tools under one umbrella, meaning you will get a consolidated single view of all the issues present in the development stage of the application. This will reduce the complexity of vulnerabilities being reported by various tools, allowing you to easily determine which vulnerabilities have been fixed and which ones are still pending.
If you are interested to learn more about Invinsense, then fill out this form and our team will reach out to you for a quick demo.
Discover complete cybersecurity expertise you can trust and prove you made the right choice!
