
If you look at the major cyberattacks that happened in organizations across the globe, they all had security tools, budgets, and people to protect themselves from adversaries.
Yet, the breach happened. Why? Because there are a lot of internal conflicts between different departments that most businesses don't address. They are not aware that these conflicts will make them more vulnerable to cyberattacks in the long run. Let's go over each of them one by one.
Every department is assigned a specific role by management.
For example, security teams handle system scanning, vulnerability detection, and risk assessment. If they see a critical vulnerability, they report it.
But for a Sysadmin, quick patching may break something, so they want to test it first.
Similarly, DevOps feels that immediate patching may require changes in the code first. Otherwise, it may later create problems in the application.
This leads to conflict.
It paralyzes the remediation, which causes the specific vulnerability to remain unresolved, which an adversary sooner or later exploits.
There Is No Clear Ownership Between IT, DevOps, and Security Teams
The security team detects a vulnerability and logs it in the ticketing system, which the IT department looks into but withholds patching it since it may affect the application that the DevOps handle, which is currently busy in a sprint and doesn’t prioritize it.
Here is an example:
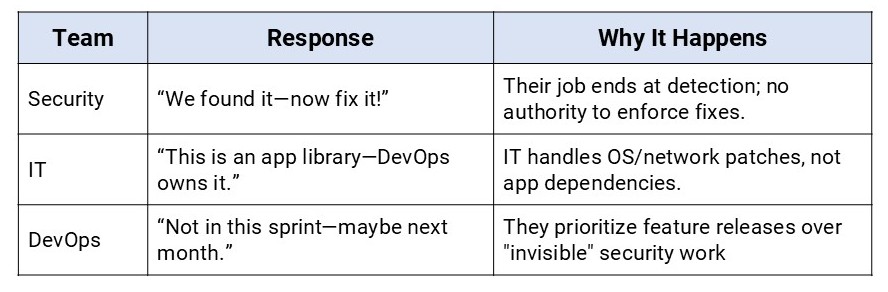
Result? The ticket keeps bouncing around without any resolution.
1) IT Department Won’t Patch Without Approval Duet o Fear of Downtime
The IT department’s core job is maintaining uptime by keeping the servers, networks, and applications running smoothly. That’s how their performance is judged.
If the system goes down, they will have to answer for it.
This brings them into conflict with the Security team when it comes to applying patches, since patching vulnerabilities requires downtime, as the system may require a reboot or to fix the compatibility issues that the patch has introduced.
Also, if the patch is not tested thoroughly and crashes the server, then they will be held accountable.
The extended downtime may upset the management, who may care more about keeping the system running rather than taking it down to fix a theoretical exploit.
"Business units scream if you take their app offline for patching, so some vulnerabilities stay open for months."
For businesses, taking down systems temporarily may impact their day-to-day work, overall productivity, or revenue. Fixing vulnerabilities may take hours, depending on their complexity, during which the application remains offline.
Many find this disruption unacceptable and prefer to delay patching to avoid downtime, which leaves the vulnerabilities exposed for weeks or months.
Most businesses want continuity; their leaders are not aware of the risk that an unpatched vulnerability carries, and there is no proper process in place for efficient patching.
2) The Pressure on DevOps to Deliver
For DevOps, speed is everything as customers expect quicker updates and fixes from them, while businesses expect newer features in the application to boost their revenues.
This brings them into conflict with the security team.
For example, due to the urgency, DevOps often wants to push code faster into the application, but the security team wants to test it for vulnerabilities first.
Security checks like this cause delays, eventually leading to conflict.
DevOps wants to use the latest library for its performance improvements, bug fixes, and new APIs. Using a newer version has its benefits: It prevents version lock, and vendors often patch known vulnerabilities in updates.
However, for security teams, newer versions often introduce newer vulnerabilities, which can become a headache. There is also compliance risk, as the healthcare and finance industries require vetted and approved versions.
This becomes another source of conflict between the two departments.
Lastly, the security team prefers immediate patching, but dependencies are a house of cards, as updating one library may break another. Also, enterprise apps are fragile as legacy systems rely on deprecated behaviors. This, yet again, creates tension.
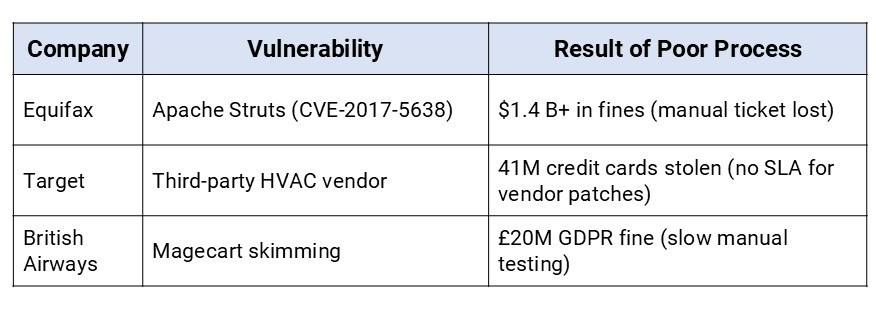
The Equifax breach happened because a critical vulnerability was overlooked as it was manually filed. No one acted upon it for months.
Similarly, in the SolarWinds Breach, adversaries remained undetected for months due to slow manual processes.
These examples show that vulnerabilities reported via email can get missed. Also, tickets sitting in Jira often end up in backlogs because no one is assigned to handle them (Should IT handle this or DevOps?). The lack of automated escalation also keeps them in a perpetual state of limbo.
Due to the absence of an SLA, there is no consensus and urgency among teams on how quickly a vulnerability should be patched. High-risk vulnerabilities should be remediated within 72 hours, but it often takes days to get resolved.
The table below shows the consequences of having no standardized process.
Modern software development and deployment processes have visibility gaps, in which DevOps hasn't fully integrated IT and Security into its workflow.
Due to this, the IT team doesn't have full oversight of what changes DevOps has pushed.
Since the IT team is unable to track deployments in real-time, the Security team also finds out at a very late stage if there are any vulnerabilities or compliance risks.
For example:
Keeping IT and Security Teams out of loop will lead to Shadow IT, Security Holes, and Compliance Failures.
We are not trying to bash or villainize other departments.
We are just trying to raise awareness in the leadership that allocating the budget and getting more tools and people for security aren’t enough.
They also need to set policies and processes that ensure timely remediation for vulnerabilities detected. Cybersecurity is teamwork, after all.
Let’s go into the solutions.
When it comes to continuous threat exposure management, the process starts not with scanning, but with a scenario:
“What if adversaries exploit a vulnerable Apache library in the customer portal?”
Build a threat model around that scenario.
Simulate potential lateral movement, evaluate the impact if the security breach happens, and measure exploitability based on real-world TTPs.
Then present a prioritized exposure report—not a list of 1,400 CVEs, but five critical vulnerabilities tied to actual risk—to IT and DevOps. Our RedOps team can help simulate these scenarios as part of Invinsense’s OXDR platform.
Suddenly, the conversation shifts from:
“Why are you interrupting our sprint?”
To
“We need to fix this before it becomes tomorrow’s headline.”
That’s what CTEM changes: It reframes vulnerability management from theoretical risk to tangible exposure. Everyone sees the same threat. And when they do, remediation happens.
Ditch the old CVSS-based process, in which everything above a score of 8.0 triggered a patching SLA. The result? Panic over low-risk issues, while an actively exploited medium-severity bug sat unpatched for 3 weeks.
Adversarial exposure validation, which is a part of CTEM, takes into account threat intelligence feeds and asset context.
Here's what organizations can do:
Don't focus on: "How severe is the vulnerability?"
Instead, ask yourself: Is someone trying to exploit this, and will it hurt us if they do?"
Remediation isn't just faster- it's smarter.
Once again, Invinsense can help you here: Our Security Engineering Team will remediate all the exploitable vulnerabilities within your application, whereas all the exploitable infrastructure vulnerabilities will be handled by the Purple Team.
With Invinsense, you will get both tools and people to address all the gaps in your organization’s cybersecurity.
Organizations shouldn’t just ask: ‘Are we patched?’
They should ask: ‘Are we exposed and are we responding to what matters?’
With CTEM, risk-based prioritization and remediation are exactly what your teams will start to do.
Discover complete cybersecurity expertise you can trust and prove you made the right choice!
