

Invinsense Deception and Activity Directory
Deception techniques - if deployed well - can be very effective for organizations to improve network defence and can be a useful arsenal for blue teams to detect attacks at a very early stage of cyber kill chain.
This blog walks through the steps of how to get alerts on deception if attacker is trying to Kerberoasting and Pass the Ticket, To Kerberoasting is a technique used in Windows Active Directory environments to extract service account credentials. This attack takes advantage of certain types of service accounts within the Active Directory that have Kerberos Service Principal Names (SPNs).
In cybersecurity, lateral movement refers to the tactics and techniques used by attackers to move through a network after gaining initial access. Once an attacker has compromised one machine or user account within a network, they attempt to move laterally to other machines or accounts to expand their control and access to sensitive data.
Pass the Hash:
Initial Compromise: The attacker gains access to a machine within the target network and extracts the password hashes of user accounts stored on that machine.
Hash Theft: Instead of cracking these hashes to retrieve the actual plaintext passwords, the attacker simply uses them directly.
Lateral Movement: With the stolen password hashes, the attacker can attempt to authenticate and gain access to other systems or resources within the network. They “pass” these hashes to authenticate without needing the actual password.
Avoiding Detection: By using hashes instead of actual passwords, the attacker can potentially evade detection mechanisms that monitor for suspicious login attempts based on incorrect passwords.
To defend against Lateral Movement and Pass the Hash attacks, organizations can implement several best practices:
Least Privilege: Ensure that users and systems have only the permissions necessary to perform their tasks. This limits the damage an attacker can do if they gain access to a system or account.
Network Segmentation: Divide your network into segments or zones and restrict lateral communication between them. This can limit an attacker’s ability to move freely within the network.
Multi-factor Authentication (MFA): Implement MFA wherever possible, as it adds an extra layer of security even if an attacker obtains password hashes.
Regular Monitoring and Logging: Continuously monitor network traffic, log activities, and set up alerts for suspicious activities, such as multiple failed login attempts.
Patch Management: Keep systems and software up-to-date with the latest security patches to protect against known vulnerabilities that attackers might exploit.
Educate Users: Train employees about the risks of phishing attacks, the importance of strong passwords, and other security best practices to reduce the likelihood of initial compromises.
In summary, Lateral Movement and Pass the Hash are techniques that attackers use to move laterally within a network and escalate privileges. Implementing a multi-layered security approach, including best practices like least privilege, network segmentation, and MFA, can help organizations defend against these threats.
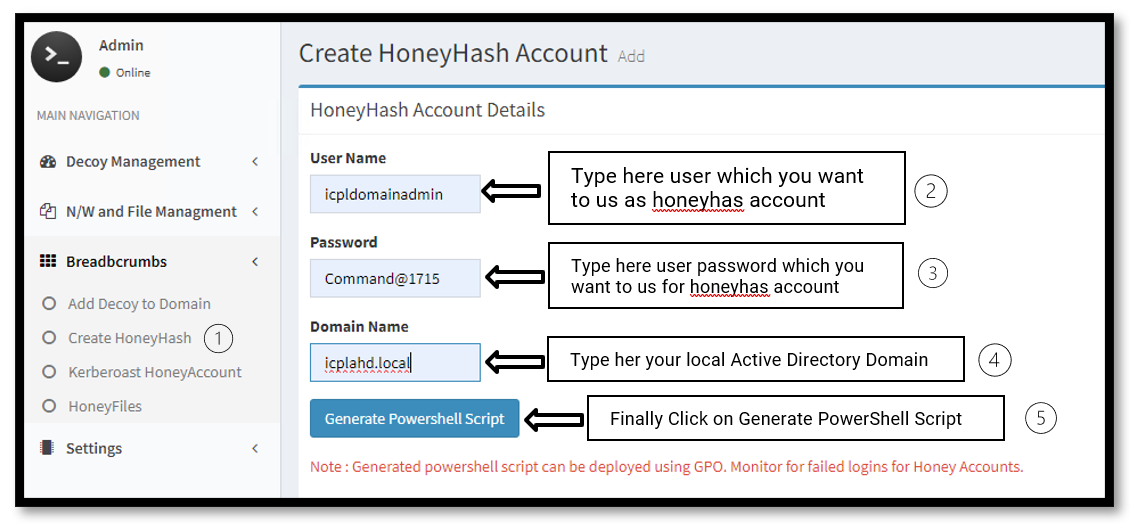

Note: Before doing this you must onboard your local endpoint, computers and Server logs on to your SIEM tool. This is important because GPO push This Honey hash account in your Computers and if the attacker tries to Access Your Endpoint using this Honey hash Account, the SecOps team can identify the attack before data or information is compromised



Discover complete cybersecurity expertise you can trust and prove you made the right choice!
