
Wazuh uses the Archive Index pattern as a method of indexing and storing logs. It is intended to assist organisations in managing massive amounts of log data effectively. A scalable and customizable method for storing logs is offered by the Archive Index pattern. It makes it possible for businesses to swiftly and simply search and analyse logs.
The Archive Index pattern is built on top of Elasticsearch, a distributed search engine that offers quick and effective searching of huge datasets. Wazuh can store logs in a form that makes them simple to search for and retrieve thanks to Elasticsearch. Data compression, which lowers storage costs and enhances search efficiency, is likewise supported by the Archive Index pattern.
Wazuh archive is a feature that allows you to automatically store security events generated by the Wazuh security monitoring platform in archive files for future analysis. It can be used to store security events that have already been processed by Wazuh and that may no longer be relevant for real-time monitoring, but that could be useful for auditing, compliance, or forensic purposes.
The Wazuh archive feature stores events in compressed files in a configurable location and format, allowing you to easily manage and access large volumes of data. The archive files are organized by date, with one file per day, and can be configured to rotate based on time or file size. Additionally, you can configure the maximum size of each archive file, the frequency of archive file creation, and the retention period of the archived data.
Step1: Change to root user Command: sudo –i
Step2: Go to filebeat directory
cd /etc/filebeat/
Step3: vim filebeat.yml and change archives enabled to true. Save and exit
Step4: Restart filebeat
Step5: Change /var/ossec/etc/
Step6: vim ossec.conf and edit “logall” and “logall_json” to yes
Step7: Restart manager
Step8: In Wazuh, go to stack management

Step9: In index patterns create a new index pattern

Step10: Name the archive as “wazuh-archives-*” and select next
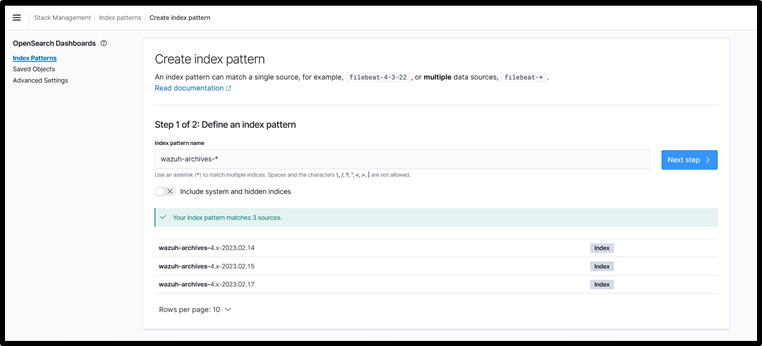
Step11: Then select time field as “timestamp” do not select “@timestamp”.
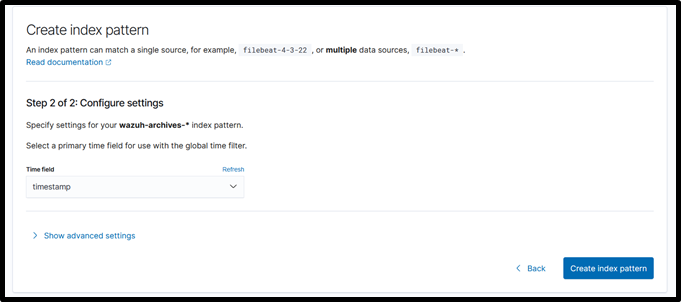
Step12: To stop archives change logall and logall_json (from step6) as no either from gui or cli and restart the manager
In conclusion, the Wazuh archive feature is a useful tool for long-term storage and analysis of security events generated by the Wazuh security monitoring platform. By enabling archive, you can store processed security events in compressed files for future auditing, compliance, or forensic analysis, without affecting real-time monitoring.The archive feature allows you to configure the frequency of archive file creation, the maximum size of each archive file, and the retention period of the archived data. The archived data can be easily accessed and managed, and can be used for incident response, compliance reporting, and forensic analysis.Enabling archive in Wazuh is a simple process that involves editing the configuration file and restarting the Wazuh service. With archive enabled, you can have a historical record of security events that can be used for analysis and compliance purposes, helping you to maintain a more secure environment.
Discover complete cybersecurity expertise you can trust and prove you made the right choice!
