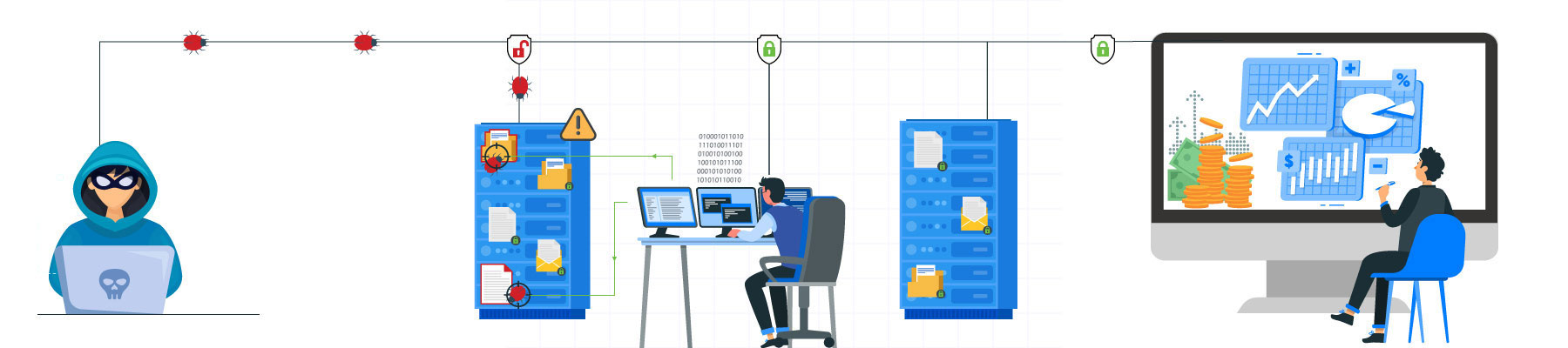
In spite of installing advanced security systems to prevent cybercrime and protect data theft, cybercriminals are usually one step ahead in tearing down the defenses. Thus it is vital to up the game and stay one step ahead. This is possible by prevention, response, or attack as the case maybe.
Financial industry provides consumers and businesses with vast amounts of services – with trillions of dollars exchanging hands daily to keep the world going. The backbone of our industrialized world is our financial institutions. Technology that has been applied to the back-end systems of banks or other financial institutions-but has since grown to encompass a plethora of other more consumer-focused applications. As of 2020, this technology (also available on your smartphone) already allows you to manage funds, trade stocks, pay for food or manage insurance. Many fintech apps are designed to connect customer finance with user-friendly technology, the term often used is Business-to-Business (B2B) technologies.
Cyber-attacks on financial institutions primarily focus on cheating people and claiming their money. Statistically it has been found that 95% of these attacks are for monetary gain. InSights revealed in their latest reports that banks and financial services organizations together comprised 25.7 percent of all malware attacks last year.
The banking industry has always been vulnerable to attacks, be it physical robberies or today’s digital campaigns targeting customer data and funds, as well as the core systems of the banks. Most commonly, these cyber attack operations are done through phishing, denial-of-service (DDos) attacks, and malware.
Fintech organisations are constantly looking for ways to enhance their IT infrastructure security, they are paying growing attention to a strategy called ‘cyber deception.’ Cyber deception involves creation of misunderstanding and redirecting the actions of a criminal, making intentional errors and undermining the effectiveness of their attack. This is done by positioning several decoys, credentials and other baits in the network of an organization and then tracking what is happening.
Financial institutions are known to have invested in advanced modern technology systems and for providing access to it. Even after major investments, gaps in security controls or human negligence / error continue to exist that prevent the effective, accurate, and early detection of breaches. A financial organisation’s compliance strength also comes with high operational overhead. There are substantial organizational and personnel costs needed to keep up with the waves of warnings and information logs on threats, all at a time when qualified employees are unprecedentedly scarce. More than ever, early detection of threats leave one in an advantageous position.
Deception shifts the game against attackers by supplying companies with a proactive response designed to foil early threats, and minimize the risk and cost involved. Highly advanced decoys and lures are designed to misdirect attackers, revealing their presence quickly, and giving them the opportunity to gather advanced forensics against their opponent.
Benefits of Deception technology based security in the finance sector-
Recent advances in deception technologies also secure the Active Directory of Microsoft with the ability to detect unauthorized queries and return false data without disrupting the environment of development. This type of manipulation misdirects attackers to a decoy, causing difficulties for them in separating true findings from fakes.
Financial organizations need to choose the providers’ best deception technologies to ensure cyber-attacks do not happen. By applying this technology, the banks will attain the full trust state of their consumers and ensure that in-services of automation are fully provided in nature. It also serves to ensure that the organizations have good governance and power, as only structures are used to administer them. There are some examples of deception technology, for example, some of them include firewalls and it helps immensely in the battle against cybercrime in financial institutions.
Infopercept has successfully deployed Deception technology in financial institutions and used advanced strategies from their Security Optimization Center that strengthen both cybersecurity and networks. These effectively ensure that threats and false positives are reduced to a minimum number. Thus, through effective process management, technology deployment and real time experience, Infopercept has acquired enough information on how to deal with and respond to the threats of cyber-attacks.
Discover complete cybersecurity expertise you can trust and prove you made the right choice!
