
In this article we will explain the arp spoof attack, which is essentially a form of man in the middle attack (MITM) and has been there for quite a long time, and in the next article we will also do a live arp spoof attack demo with the right tools.
Man in The Middle Attack:
Most of you would have guessed the meaning of the name itself.
According to Wikipedia, a man-in-the-middle attack (MITM) This is an attack in which the intruder secretly relays and probably changes the contact between two parties who think they communicate directly with each other. Let’s take an example.
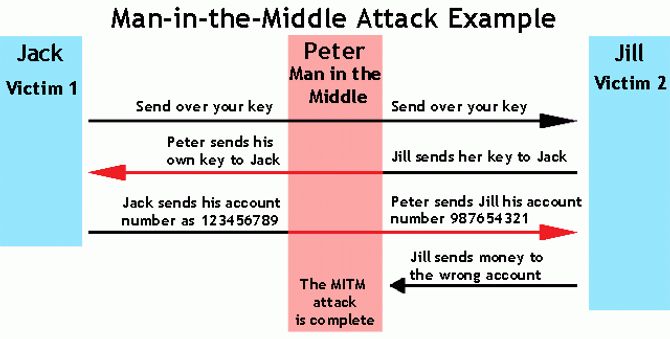
Now you’ve got to have an idea of the attack.
ARP:
ARP is a protocol for address resolution. It is essentially a protocol that the IP uses, specifically IPv4 to map IP addresses to MAC addresses that a data link protocol uses.
How it works:
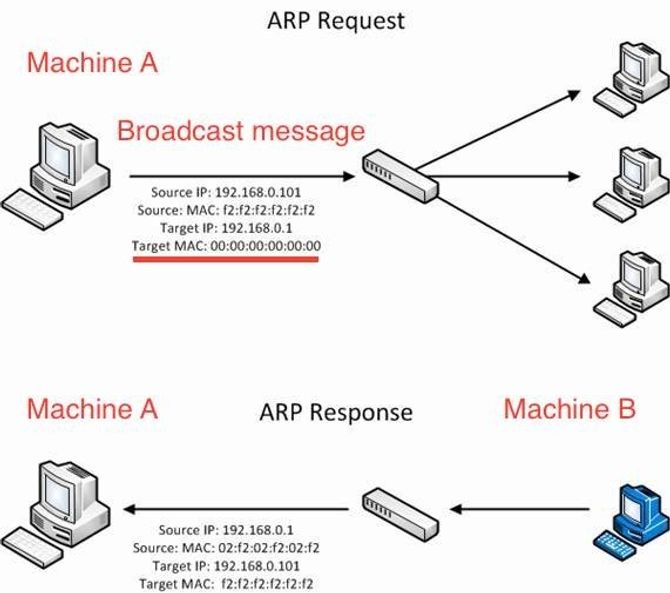
Every program has an ARP table where information about which IP address is associated with which MAC address is stored. The program will first search the ARP table when sending a packet to an IP to see if it has MAC address associated with that IP. Let’s say Comp A (192.168.1.4) wants to send IP packet to Comp B (192.168.1.5). Yet Comp A has no knowledge of Comp B’s MAC address.
So A would send in the network an ARP request message as “192.168.1.5 belongs to whom?”. Comp B upon receiving this would store A’s IP address and MAC address in its own ARP table and respond that “192.168.1.5 belongs to me” and give the MAC address itself to A along with that. So A will store it in its own ARP table after acquiring B’s IP and MAC. Today, as source IP, MAC and Destination IP, MAC is established, the IP packet can be successfully transferred.
You can also check your arp table using the following command in your CMD: arp –a
ARP Spoofing/Poisoning:
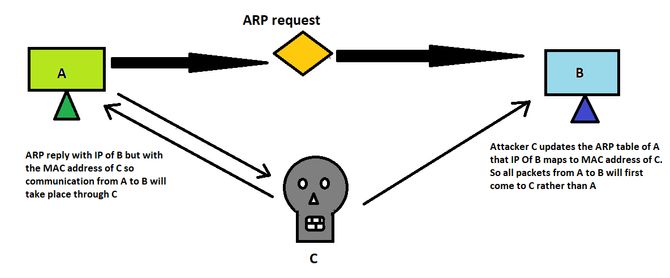
Comp A can send IP packets to Comp B because A’s ARP table assigns B’s IP to B’s MAC address. So there would be contact.
Now suppose an attacker C would send an ARP answer with B’s IP but with its own MAC address (i.e. C’s MAC address). And since ARP has no authentication method, it will change the A’s ARP table with the IP address of B maps to attacker C’s MAC address.
So A will go to C when you give some packet to B. Now C will delegate a forwarding function to forward the same packet from C to B, thus launching a Man in the middle attack where C is in the middle and seeing all the requests.
Countermeasures:
See you next time.
Discover complete cybersecurity expertise you can trust and prove you made the right choice!
