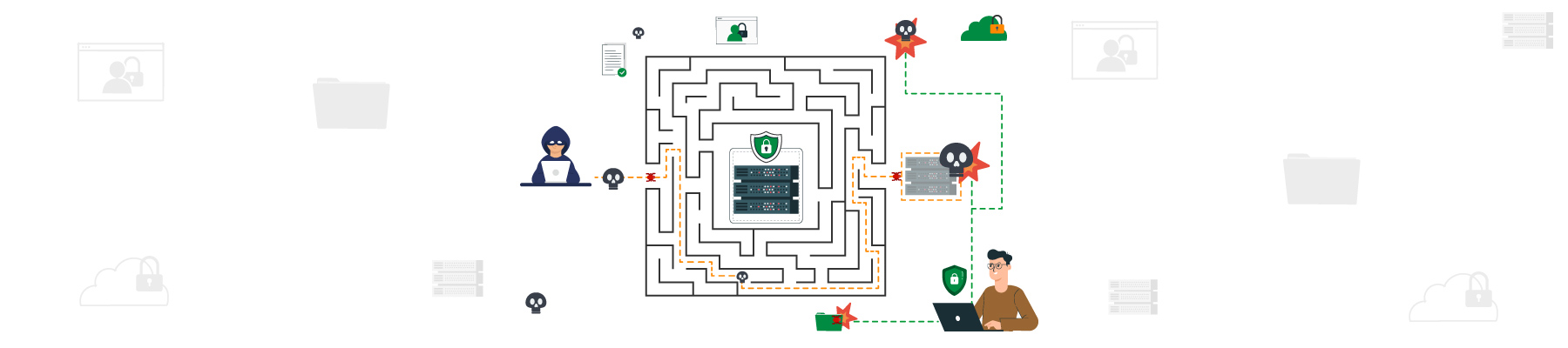
Impact of Computer Viruses:
All computer systems are susceptible to virus attacks. Even government websites and highly coded top military sites are not immune to it. Some of the viruses that are notorious in nature include Morris Worm, Trojan etc. With evolution in technologies, there are noticeable changes in fields like Banking Malware, Key-logger, Bitcoin Wallet stealer, Android hack, and much more.
History has taught us that a well-orchestrated virus attack could lead to losses to the tune of billions of dollars. As the world is fast progressing towards and depending more and more on technology, it is imperative to not only keep up but stay a step ahead as far as preventing such attacks in the future.
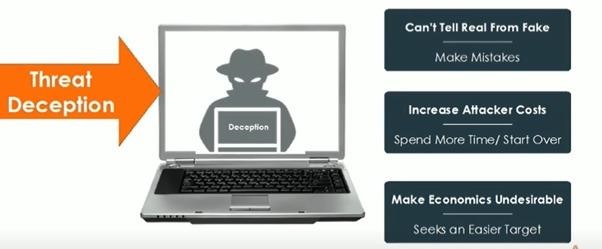
Deception Technology can be a gamechanger as more sophisticated technologies like Artificial Intelligence and other advanced machine learning systems are used to defend digital assets from the attackers. It works by setting up traps or decoys for the hackers to trick them into believing they have hacked into the system. What we would have actually done is build perimeter defences according to our preferences or design which ultimately merge into the network.
Early breach detection is the key to the successful implementation of Deception Technology.
It uses visibility and attack path as a two pronged approach to tackle the violation of the infrastructure.
Deception technology is easier to deploy on some devices than others. These devices have less memory to install the traditional cyber security apps/agents, the firmware or have compatibility issues. This makes it especially suitable for Internet of Things (IoT) devices, legacy systems and industry-specific devices as well.
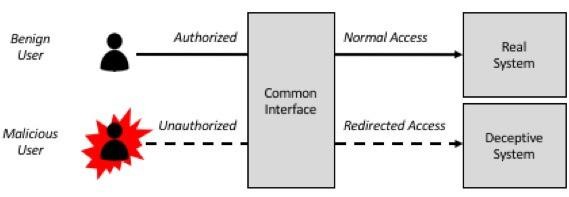
The pattern for any misleading framework is direct. Favourable and vindictive clients each enter a typical interface, despite the fact with plans to exist where the beguiling interface is an escape from the run of the mill work processes, which features anybody truly searching for a section point. The normal interface at that point incorporates usefulness that sidetracks access to the tricky framework through utilisation of misleading baits and distractions. This is an influential idea that changes the idea of digital security hazard to the executives.
To get ready, send, and operate deceptions, present day DDPs use machine self-figuring to see new gadgets going ahead and off the system, alongside their profiles and traits. Initially intended for making genuineness, this data likewise furnishes security groups with incredible information on adds and changes to the system.
This has proved priceless for distinguishing unapproved individual gadgets, IoT, and different less-secure gadgets being set on the system, or gadgets included with malevolent aim. Notwithstanding gadget perceivability; stages additionally accompany the capacity to caution on uncovered accreditation assault ways.
Uncovered and stranded qualifications, alongside framework misconfigurations, are frequently the opening required for an aggressor to increase a solid footing. The understanding gave in land maps lessens hazard as well as takes out long periods of manual handling work.
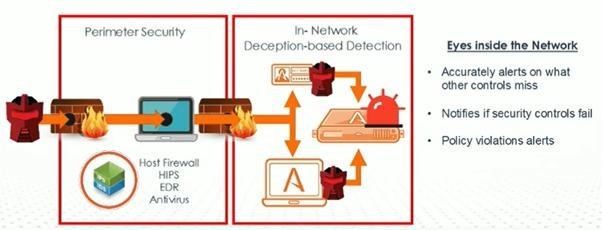
EARLY & ACCURATE DETECTION
The deception of threats offers and provides early detection of breaches to the network or to the particular system whether it consists of external, internal, or 3rd party attacks. Real-time threat detection of reconnaissance and credential theft activities can be achieved as attackers are deceived into engaging with decoys, deception lures, and bait designed to entice hackers into revealing themselves to the respective authority.
DETECTION OF KNOWN & UNKNOWN ATTACKS
It is not reliant on signatures or pattern matching, but accurately detects in-network reconnaissance, credential theft, Man-in-the-Middle attacks, and lateral movement of threats that other security controls miss.
Deception technology is relatively very simple to be built in-house but at the same time it gets very difficult when we have to make it convincing. It is imperative to make the decoys as realistic as possible.
Several tactics that are used in deception technology are as follows:
The key to prevent any kind of data compromise lies in advance detection of threats. Infopercept supports different types of decoys at various levels be it while trying to steal credentials or break into network connections. These decoys prevent the hacker from going deeper into the network. Once the decoy server has been attacked, a trigger is alerted at the deception server. This server helps identify which server the hacker has attacked and what attack vectors were used.
The Security Optimization Center (SOC) at Infopercept takes care of all your security needs leaving you to focus on your organizational goals. It uses a three pronged approach of Security Monitoring, Incident Response and Threat Intelligence.
Discover complete cybersecurity expertise you can trust and prove you made the right choice!
