In Assumed Breach Testing we test in a way where we already have a limited access into the Network. That can be provided by client in number of ways including VPN to their Network or a machine in their environment which we can have access to. Assumed Breach Testing is an essential component of an organization’s cybersecurity strategy. It helps to identify potential security risks and vulnerabilities in internal network and to develop strategies to strengthen the security infrastructure.
The goal of Assumed Breach Testing is to identify vulnerabilities and weaknesses in an organization’s security infrastructure by assuming that the attacker has already breached the perimeter defenses and is operating inside the network.
1) Identified Vulnerabilities: The report will outline the vulnerabilities that were identified during the testing process. This may include details such as the vulnerability’s severity, the potential impact on the organization, and the likelihood of exploitation.
2) Exploitation Attempts: The report may also include details about the number of attempts made to exploit the identified vulnerabilities, the techniques used, and the level of success achieved.
3) Network Architecture: The report may provide an assessment of the organization’s network architecture and topology, highlighting any weaknesses or vulnerabilities that were identified.
4) Security Controls: The report may provide an evaluation of the effectiveness of the organization’s security controls, such as firewalls, intrusion detection systems, and antivirus software.
5) Incident Response: The report may provide an assessment of the organization’s incident response capabilities, including the effectiveness of the response process and the coordination between different teams.
6) Recommendations: The report may provide recommendations for remediation strategies to address the identified vulnerabilities and weaknesses. These recommendations may include technical controls, policy changes, or user awareness training.
It’s important to note that the findings in an Assumed Breach Testing report may be different depending on the scope and objectives of the testing, as well as the specific tools and techniques used. However, the report should always provide a clear and actionable summary of the vulnerabilities and weaknesses identified, along with recommendations for remediation.
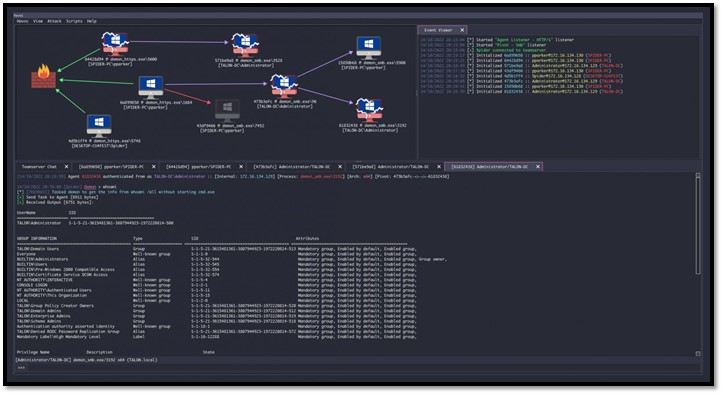
1) Misconfigured Systems: Misconfigured systems are a common vulnerability that can be exploited by attackers. During an ABT, misconfigurations in servers, databases, or other systems may be identified.
2) Weak Passwords: Weak passwords are another common vulnerability that may be identified during an ABT. This includes default passwords, easily guessable passwords, and passwords that are not regularly changed.
3)Missing Security Patches: Missing security patches can leave systems vulnerable to known exploits. During an ABT, missing security patches in servers, applications, and other systems may be identified.
4) Unsecured Ports and Services: Unsecured ports and services can provide attackers with a pathway to gain access to systems. During an ABT, unsecured ports and services in servers and applications may be identified.
5) Lack of Logging and Monitoring: Lack of logging and monitoring can make it difficult to detect and respond to security incidents. During an ABT, the effectiveness of logging and monitoring systems may be tested.
6) Outdated or Unsupported Software: Outdated or unsupported software can leave systems vulnerable to known exploits. During an ABT, outdated or unsupported software in servers and applications may be identified.
One of the key objectives is to identify vulnerabilities that allow an us to move laterally within the network and gain access to sensitive data or systems. Lateral movement refers to the process by which an attacker gains access to a system or resource that is located beyond the initial point of entry. During the assessment we will try to do Lateral Movement and Pivot from one System to another and the end goal will be to have the full control over the Internal Network and find ways through which we can bypass Security Mechanisms which are in place like EDR, Firewalls, IDS, IPS, AD Logs, etc.
Overall, the goal of identifying vulnerabilities related to lateral movement and security mechanism bypass is to help organizations understand the potential impact of a sophisticated attacker who is intent on accessing sensitive data or systems. By identifying and addressing these vulnerabilities, organizations can take steps to strengthen their security posture and reduce the risk of a successful attack.
Discover complete cybersecurity expertise you can trust and prove you made the right choice!
