.avif)
IT systems play a crucial role in the day-to-day functioning of any organization, so any disruption within these systems can severely paralyze the entire company.
Maintaining their security was paramount; therefore, to protect them, admins relied on two tools: SIM (Security Information Management) and SEM (Security Event Management).
One focused on analyzing security data for compliance purposes, while the other provided real-time monitoring of security events.
This was in the 2000s, but as the technology evolved, the newer IT systems began to produce huge volumes of data that started to become a headache for administrators.
It was becoming increasingly difficult for them to maintain the security of these systems.
SIEM arose to address this problem.
It combined both SIM and SEM, which gave administrators a centralized platform to collect, analyze, and respond to security events from across an organization's IT infrastructure.
Furthermore, SIEM also integrated other features like threat intelligence, user entity and behavior analytics, and incident response capabilities. It became a useful tool for recognizing security threats, vulnerabilities, and suspicious behavior in users.
Also, it automated manual processes that were involved in threat detection and incident response.
We are now in 2024, and legacy SIEMs are fast becoming obsolete, and companies need something to survive in today’s cybersecurity landscape.
That’s the thing with technology; either it evolves or gets discarded in the graveyards of technology.
It’s time for companies to ditch the legacy SIEM and embrace Invinsense XDR to secure their systems. Why do we say this? Well, there are many reasons. First, let's start with the poor detection of Legacy SIEM.
Poor Detection of Adversary Techniques
One of the major problems that have been found in legacy SIEM is that they are unable to detect the majority of MITRE ATT&CK techniques, even though it has all the data for it.

“A cybercriminal breaches the company's defenses and gains unauthorized access to a treasure trove of sensitive customer data”
This has busted the claim that lack of data is the problem, which it is not. Misconfigured data sources, missing fields, and parsing errors are the major reasons why the SIEM doesn't fire an alert.
But what could be the reason behind these misconfigurations?
First of all, over the years, SOC has become increasingly complex as organizations are using dozens of different security tools that come with their own logs/events/alerts for which detections have to be set up based on understanding how these tools work. This is a gigantic task in itself.
Furthermore, nothing remains the same. Whether it is infrastructure, security tools, attack surface, adversary techniques, or business priorities. This creates a constant mess in security configurations, which is why Gartner has predicted that the majority of cyberattacks in the future will happen due to misconfigured settings.
Lastly, every company is unique and needs cybersecurity that is on par with their needs. So, one size fits all from SIEM vendors will not work here.
Also, legacy SIEM depends on people, so if you want to maintain and scale it for better detection, then you need a team of skilled employees who have expertise in it. Otherwise, it's not possible.
The problem is that most companies live in a false sense of security. They don’t realize that there is a major gap between theoretical and actual security within the organizations.
Too Many False Positives
Due to legacy SIEM, SOC analysts experience an overwhelming number of alerts, which can take a lot of time to investigate.
If you want a general idea, then let’s say that out of 10 minutes, 5 minutes goes into gathering data and getting the complete picture of the incident.
In terms of collecting essential information regarding the asset that is at risk, it will take a SOC analyst approximately 3 hours daily to gather everything, which is quite a waste of time.
Furthermore, SOC analysts investigate 10+ security alerts on a daily basis, out of which 50% turn out to be false. This frustrates them, and they often end up ignoring the alerts and turning them off.

“A frustrated Security Operations Center (SOC) analyst is overwhelmed by the incessant stream of alerts flooding in from the SIEM tool”
This can be quite dangerous if there is a real alert regarding an actual attack.
This feels similar to the story we all heard in our childhood, where a young boy repeatedly lies about a wolf attacking the sheep just for fun. When a real wolf comes, no one believes him, and the sheep are scattered. Legacy SIEM has become just like that.
SOC’s main job is to identify and remediate threats. But now it is becoming more and more about managing constant alerts that keep coming in. This forces them to focus more on reducing the alerts rather than doing their job to manage potential threats and incidents that may happen within the organization.
Legacy SIEM Are Too Expensive
Initially, the legacy SIEMs were useful in analyzing the data generated by the machine. This helped the security teams in mitigating potential attacks. However, the problem began when its pricing model was linked with how much volume of data the machine generated. So, it can quickly become extremely expensive for companies if their tool generates too much data.

“The CFO is visibly tense and concerned upon viewing the bill attributed to the excessive data generated by the legacy SIEM”
To remedy this problem, the security teams were forced to limit how much data they ingested, but this left the company more vulnerable to cyberattacks as this data was valuable in mitigating potential attacks.
The cost of SIEMs varies depending on an organization's infrastructure.
The infrastructure of an organization plays a crucial role.
For example, small and medium businesses may have to shell out between $10,000 to $100,000 per month for a SIEM, which can really break their banks.
Most organizations often end up overpaying for their SIEM.
Furthermore, SIEMs need a 24/7 SOC team to manage this technology, need to be deployed properly and have to be constantly kept up to date. They also have to integrated into cybersecurity architecture.
All of this will increase the financial burden on small to medium size organizations.
Top Reasons Why You Should Choose Invinsense XDR to Secure Your Organization
There are many reasons why you should choose Invinsense XDR for your business instead of legacy SIEM.
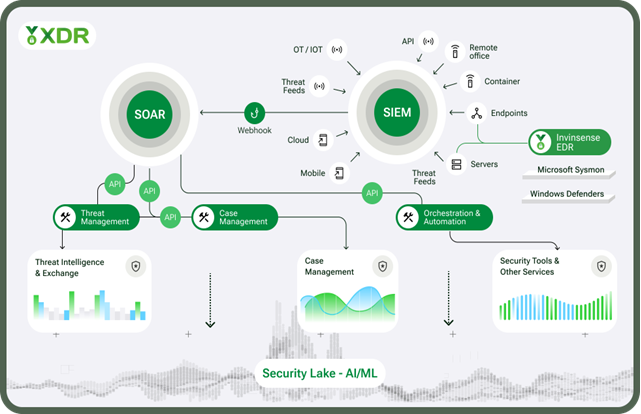
Firstly, Invinsense XDR brings all security tools into one platform. It combines SIEM, SOAR, EDR, Case Management, Threat Intelligence, and Threat Exchange, which will eliminate the need to contact different vendors to get these services.
This will also prevent silos that exist due to these different vendors, thus optimizing and strengthening your organization’s overall cybersecurity posture.
Secondly, Invinsense will not spam your team with constant alerts that will ultimately annoy them. It will prioritize which alerts are truly dangerous and will focus on those first, thus putting the SOC analysts in a better position to mitigate potential attacks on your organization.
We will even patch up any vulnerabilities or loopholes that caused the alert.
Furthermore, Invinsense XDR follows the OODA principle. During cyberattacks, people often freeze and are unable to react quickly. But with the help of Invinsense, your team will be able to make quick decisions.
This also solves one crucial problem that I highlighted above, which is the one-size-fits-all approach in cybersecurity. Since every organization is different, Invinsense, with its OODA approach, can be customized by companies as per their requirements.
If your organization uses different security tools, then Invinsense XDR also provides API integrations with 200+ vendors. It also offers unlimited storage and computing capacity through a security lake.
Invinsense XDR will work as a defender's brain for your organization’s cybersecurity posture.
If you want to learn more about Invinsense, then schedule a demo by filling this form and our team will reach out to you shortly.
Discover complete cybersecurity expertise you can trust and prove you made the right choice!
