Hi folks,
Last time we wrote about how to prove concepts We noticed some vulnerabilities in cross-site scripting in a CMS that led to CVEs . we will post another POC on a Cross Site Scripting Vulnerability present in a Dell subdomain in this report.
This weakness that I recorded was a long way back in October 2017 and it was my third bug that I admitted after Intel and Avast, so it’s something really special for me.
Now coming to XSS,
Cross-Site Scripting (XSS) attacks are, according to the internet, a form of scripting that injects malicious scripts into otherwise benign and trusted websites. XSS attacks occur when a web application is used by an attacker to send malicious code to a different end user, usually in the form of a browser side script. Flaws that allow such attacks to succeed are common and occur wherever a web application uses a user’s input within the output it produces without validating or encoding it.
An attacker may use XSS to give an unsuspecting user a malicious script. The client of the end user has no way of knowing that the script should not be trusted and that the script will be executed. Because it thinks the script came from a trusted source; the malicious script can access any cookies, session tokens, or other sensitive information retained by the browser and used with that site. Such scripts can also rewrite the HTML page text.
We will be making a detailed explanation on XSS in the coming days that will be put on the articles page.
Then I started to move on with the universal reconciliation process that everyone is pursuing.
So I used google dorks to find out some of the subdomains below is the google dork we could use to find out about specific subdomains of a particular website.
Site:*.dell.com -www
But there are many other feasible resources that we could also use to enumerate subdomains, such as Sublist3r, Knockpy, and some online websites such as Virustotal.
I landed on the following subdomain after checking several subdomains:-
The website was dedicated to providing the public with customer support.
It had two steps.
I had to write a message with our email I d in the first stage and then click on the next one.
This led me to phase 2 which was a form for contacting us that looked like this
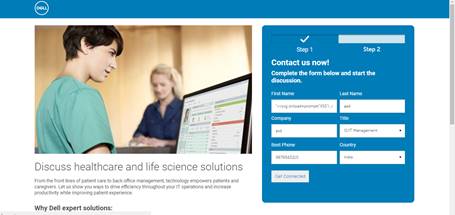
There have been various input fields such as first name, last name, business, title etc … so too many input fields … a good place to test our XSS payloads?
So I arbitrarily filled in the information and thought about putting an XSS payload in the first name input field
And I clicked on the next button after filling out the other info, which then brought me to a Thank you page and along with that, I got a magical XSS popup.
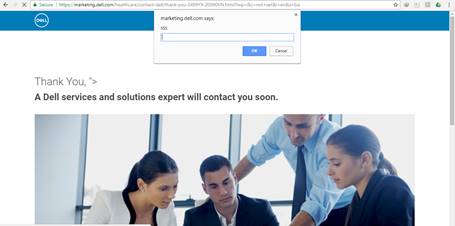
I quickly prepared a report regarding the security issue and mailed it to: Vulnerability_Research@dell.com
And they fixed the issue after months of discussions and put my name on their Protection Acknowledgement page

Link to their Security Acknowledgement Page:
https://www.dell.com/learn/nz/en/nzbsd1/campaigns/contributors-dell-software-security
Timeline
So that’s for now. See you next time. Goodbye
Discover complete cybersecurity expertise you can trust and prove you made the right choice!
