.png)
Recently, Boeing revealed that the LockBit ransomware gang had demanded $200 million as an extortion payment after breaching the company’s network and stealing sensitive data last year.
What does this tell you? Even big organizations with one of the best cybersecurity infrastructures can get breached.
How will smaller companies fare then in front of such dangers
Today’s digital world is a warzone in which cybercriminals relentlessly try to breach organizations to steal data, as it is the new oil that everyone is trying to harness for their benefit.
Companies need to realize that sooner or later, there will come a time when adversaries will come after them.
How successful they will be in fending off the attack depends on whether they have identified vulnerabilities on time and patched them out. However, the core problem is that most organizations have a too lax attitude when it comes to assessing their infrastructure for weaknesses and loopholes. By the time they do become aware, it’s too late, as the attack has already taken place.
If you want to protect your organization, then first, you need to become aware of the vulnerabilities that exist in your systems. For that, you are going to need the help of red teaming.
Red teaming involves testing an organization’s defenses by launching attacks in a controlled environment, just like how adversaries do. This helps the organization identify vulnerabilities in its infrastructure, which it can then patch up, making the entire company more secure in the long run.
You must have come across the phrase “Fighting Fire with Fire.” This is exactly what the red teaming is all about. When it comes to cybersecurity, prevention is better than cure, and red teaming plays a crucial role in that.
In this blog, we are going to talk about the increasing importance of red-teaming in this weird age we are currently living in.
But first, let’s talk about how dangerous the digital world has become ever since the dawn of the internet.
The American West was considered the Wild West due to being lawless. This was because people there disregarded official laws and committed crimes such as theft and murder.
Similarly, the Internet is the modern Wild West as cybercriminals continuously break the laws and ruthlessly conduct cyberattacks to steal confidential data that can bring any organization to its knees.
Take, for example, the zero-day exploit, which is a major threat to all organizations nowadays.
Imagine your company is hard at work building software for the customers, but it has a bug that nobody on your team is aware of yet. Before your team could find out, a group of hackers discovered it and created a program to exploit this vulnerability, allowing them to steal your organization’s sensitive documents, emails, or source code and sell them to the black market for a lump sum of money.
Incidents like these are called zero-day exploits. The dangerous fact is that you and the team will never even find out about it until the adversaries themselves reveal it.
Even software companies want it to make their application more secure.
In 2023, at least 97 zero days were exploited in the wild.
There is a black market for it in which brokers offer huge amounts of money on behalf of their clients to buy it. The below screenshot shows that they are offering millions of dollars for these exploits.
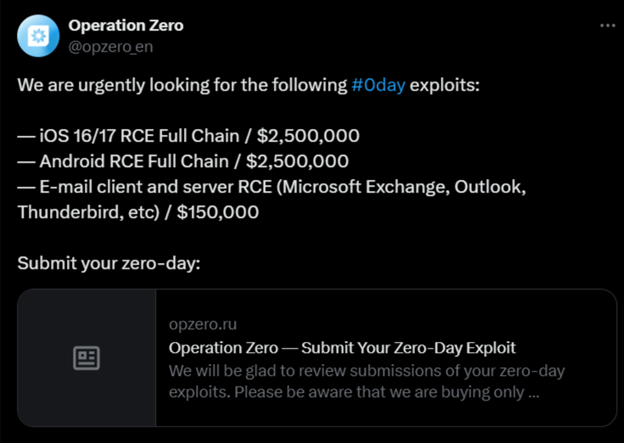
What if hackers sell the zero-day exploit of your software to rivals and competitors? They can harm your organization in many ways:
● Disrupt your product launch, which can tarnish your company’s reputation and give rival companies a competitive advantage in the market. For example, they might introduce their product just at that time as an alternative.
● Steal your confidential data, which your competitors can use to improve their products and gain an advantage over your organization.
These are just some of the scenarios, but they will give you an idea of how dangerous zero-day exploits can be for your organization.
On a country level, Iran’s nuclear facilities were sabotaged through a zero-day exploit called Stuxnet. It was capable of disrupting the entire country’s electrical grid.
Since everything runs on software nowadays, imagine you are driving your car to the office, and suddenly, you lose control over it. Its brakes and steering are no longer working, and the car is being remotely controlled by a hacker who used a zero-day exploit to gain control over your car. Sounds nightmarish, isn’t it? But that’s a real possibility since modern vehicles are packed with software with their zero-day vulnerability.
A successful cyberattack can be devastating for any organization. In the next section, you will find out why.
This incident happened in 2014 and is quite well known. A notorious group of hackers calling themselves “Guardians of Peace” leaked confidential data belonging to Sony Pictures Entertainment.
The data included personal information of employees (along with their families) who are working for Sony, like their social security numbers, names, contact details, phone numbers, date of birth, email addresses, employment benefits, worker compensation details, retirement, and termination plans, previous work history of employees, executive salaries, medical plans, dental plans, genders, employee IDs, sales reports, copies of passport information and receipts for traveling by employees worldwide.
It also includes:
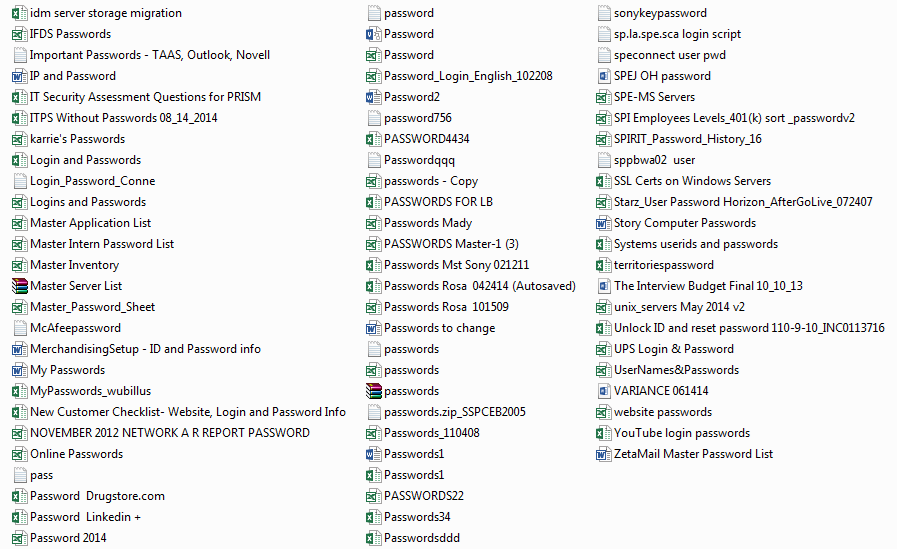
Furthermore, the data leak also contained information on security certificates, internal and external account credentials, and authentication credentials with plaintext passwords for systems such as the YouTube page of Sony and UPS accounts.
The screenshot below shows how these files were kept.
The attack was so intense that Sony Pictures was forced to shut its network down and went completely offline to repair the damage.

The US government blamed North Korea for the attack as a film was about to be released (The Interview), which depicted the assassination of Kim Jong Un, the supreme leader of the country.
Although, many within the cybersecurity circle feel skeptical and don’t believe in this claim. Many feel that it was done by a hacker who was just bored.
However, this incident showed how one attack can completely paralyze a company.
Sony had to pay $15 million to deal with the damage due to the hack. It had to halt the release of its film, which eventually came out through online digital rentals and limited release at selected theatres.
Furthermore, a lawsuit was filed by former employees against the company over the loss of their data due to which the company had to pay $8 million to settle the case.
This incident happened because Sony was extremely careless in securing itself.
Also, it’s not like organizations have learned any lessons from this attack, as cyber-attacks continue to happen, for example:
Most organizations fall prey to cyber-attacks like the above ones we highlighted due to:
With the launch of ChatGPT in 2022, we are seeing a new gold rush of generative AIs, with every major corporation developing its Gen AI product. Nowadays, creating content, images, and videos is just one prompt away, thanks to artificial intelligence.
It’s a technology that has made people feel both excited and nervous.
Any piece of technology can be misused, and generative AIs are no exception. For example, tools like ChatGPT and Bard, are trained on large amounts of data. These datasets act as a repository from which the tool generates the answer for your prompt.
Now, imagine a cybercriminal who has the data on all common types of malware that exist today. They can use this data to train the AI to create the most potent malware to attack your organization.
Just like how in the news, we keep seeing new variants of COVID-19 emerging, similarly, we might see new malware variants that are more difficult to detect by the existing cybersecurity mechanisms.
Furthermore, AI can also be used by adversaries to manipulate the people. It can use data to create personalized messages that a cybercriminal can use to dupe someone.
One of the major problems that we face today is our data not being in our control. None of us knows or cares how it’s being used by the organizations with whom we freely share our data or where it is getting shared.
Imagine a person who is looking for a job desperately based on the public information available. This data can be exploited by an AI to create a perfect phishing email that contains a job offer. The cybercriminal will then use it to lure the person in and commit fraud.
The success rate of phishing attacks has risen from 18% to 51% due to the increasing use of personalized messages.
As we have said at the start, the majority of cyberattacks happen due to organizations’ inability to detect and respond in time. By the time they do become aware, it is already too late.
This reminds us of Greek Mythology, where Cassandra, a Trojan princess, was cursed by Apollo to always see the future accurately, but never be believed by anyone. This applies equally to organizations nowadays.
● Just like Cassandra’s prophecies, security analysts identify potential threats and vulnerabilities within the organizations.
● Management ignores the warnings due to lack of urgency, budget constraints, or simply not understanding the gravity of the situation (like the Trojans ignoring Cassandra)
● When the attack finally takes place, organizations suffer significant damage because they didn’t act in time, just like the Trojans did when the Greeks landed on their shore.
To deal with this problem, Invinsense OXDR has put together different offensive security tools in one place to help your organization better predict and respond to future attacks.
Just as adversaries follow a four-phase methodology when attacking an organization, Invinsense OXDR also has a four-phase process to deal with the attacker at every level.
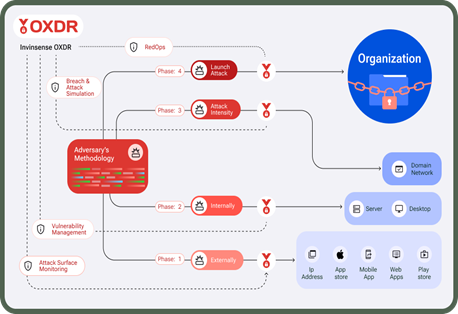
In phase 1, Invinsense OXDR will continuously monitor external access points like IP addresses, App Store, Mobile Apps, Web Apps, and Play Store.
This is because adversaries will often try to attack your organization through these access points. For example, they may create a duplicate application that your organization uses, upload it to the app store, and use it to dupe your employees.
In phase 2, Invinsense OXDR will perform a vulnerability assessment on your organization’s servers and desktops that employees use for their work to detect any weakness that the adversary can exploit.
In phase 3, Invinsense OXDR will simulate actual cyber attacks (through tactics, techniques, and procedures used by adversaries) to test your organization’s security posture and see how well it will fare in the face of an actual attack.
In the final phase, Invinsense OXDR will launch an all-out attack (more intense than previous ones) using actual attacker techniques. This will reveal whether your organization is prepared enough to fend off an actual attack. This phase will also identify areas of improvement needed in your infrastructure.
Once all this is done, our team will prepare the final report and hand it to you for assessment.
Discover complete cybersecurity expertise you can trust and prove you made the right choice!
