
In today’s Era, cyber-security is a critical concern for organizations of all sizes. The frequency and sophistication of cyber-attacks have been on the rise, and companies are under immense pressure to secure their digital assets from potential threats. Penetration testing is one of the most important measures that organizations can take to assess their security posture and identify vulnerabilities. However, traditional penetration testing methods can be expensive, time-consuming, and limited in scope. Open-source penetration testing tools offer a cost-effective and flexible alternative, empowering organizations to take a proactive approach to security.
Open-source penetration testing tools provide several advantages over proprietary solutions. Firstly, they are often free or significantly cheaper than commercial software. This can make them more accessible to smaller organizations or those with limited budgets. Secondly, open-source tools are often more flexible, allowing customization and tailoring to meet specific requirements. Thirdly, open-source tools are constantly being developed and improved by a global community of developers and users, providing the benefits of peer review and a diverse range of perspectives.
One of the most popular open-source penetration testing tools is Metasploit. Metasploit is a powerful framework for exploiting vulnerabilities in networks and applications. It provides a range of modules for penetration testing, including payload delivery, auxiliary modules, and post-exploitation modules. Metasploit is widely used by security professionals and has a large community of contributors who contribute to its development and maintenance.
Nmap is another well-known open-source programme. Nmap is a network scanner that may be used to inspect or find hosts and services on a network as well as find weaknesses and potential attack points. Nmap is extensively used in the security field and can be customised with a variety of scripts and plugins.
OpenVAS is another open-source tool that provides vulnerability scanning and management. OpenVAS is a fork of the Nessus vulnerability scanner and offers a similar feature set. OpenVAS is free and open source and is widely used in enterprise environments.
Other many open-source tools are used for penetration testing include Wireshark, a network protocol analyzer, and Aircrack-ng, a suite of tools for assessing Wi-Fi network security.
Open-source penetration testing tools are not without their challenges. Firstly, they require a certain level of technical expertise to use effectively. This can be a barrier to adoption for some organizations. Secondly, open-source tools can sometimes lack the same level of support and documentation as commercial software. However, many open-source tools have active communities and support forums where users can ask for help and share knowledge.
An automated recon suite for web applications with a focus on highly flexible, simplified recon via Engines, recon data correlation and organisation, continuous monitoring, supported by database, and simple yet intuitive User Interface.
https://github.com/yogeshojha/rengine
An open-source, free tool called reNgine provides a number of functions for web application reconnaissance. ReNgine aims to close the gap in the traditional recon tools and is probably a better alternative to currently available commercial tools thanks to its focus on a highly configurable, streamlined recon process via engines, recon data correlation, continuous monitoring, recon data backed by a database, and a simple yet intuitive user interface.
The usage of engines by reNgine to speed up the reconnaissance process is one of its most potent characteristics. A module called an “engine” specialises in a certain area of reconnaissance, such as subdomain enumeration, port scanning, or vulnerability scanning. ReNgine offers a very adjustable and effective reconnaissance procedure by letting users specify the engines they want to use.
Correlation of recon data is another potent aspect of reNgine. The data collected by reNgine’s engines is automatically correlated, giving users a completer and more accurate picture of the target system or network. This can be used to find potential attack paths and weaknesses that conventional reconnaissance tools might overlook.
Additionally, reNgine provides ongoing monitoring features that let customers schedule scans and receive alerts for any modifications or brand-new discoveries. This guarantees that any possible security concerns are found and resolved quickly.
Additionally, the database that supports the recon data provided by reNgine enables users to quickly store, search for, and evaluate the information obtained throughout the reconnaissance process. For upcoming audits and evaluations as well as continuing monitoring of the target system or network, this can be immensely helpful.
Setting up ReNgine
• Kali Linux
• Docker
• Installation
Installation is quite simple but we need to meet some requirements of this tool. First, we download the tool from GitHub using the following command. We need to go to the directory after which we will install some other tools.
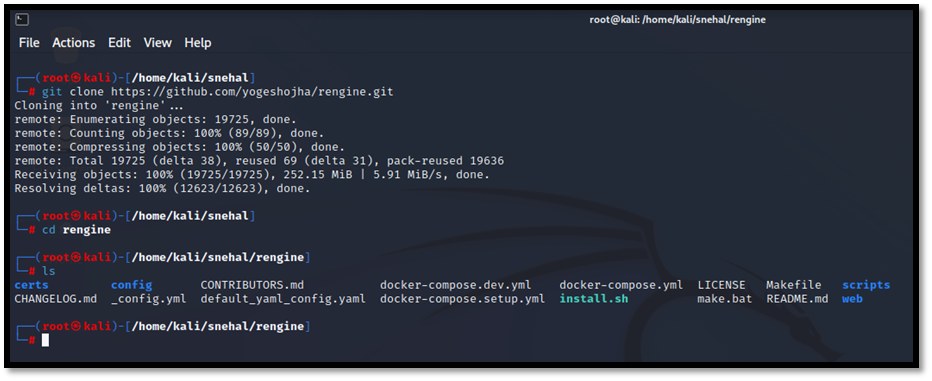
git clone https://github.com/yogeshojha/rengine.git
cd rengine
is
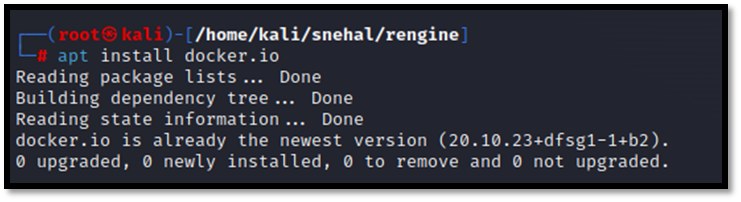
We have to download the docker using the following command, which is necessary for the tool.
apt install docker.io
The installation is almost done, now we will start and enable docker using the following command.
systemctl start docker
systemctl enable docker

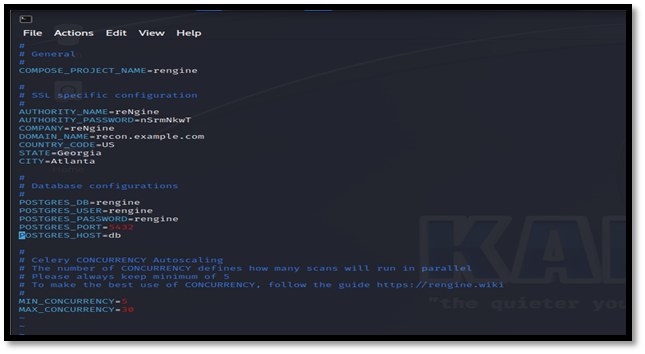
Change the PostgreSQL POSTGRES PASSWORD password when editing the dotenv file!
Vim .env
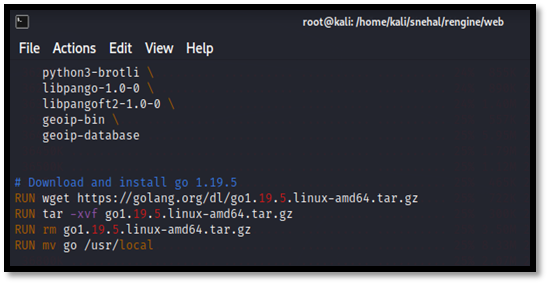
Now we need to check go version and change it from go 1.18 to go 1.19.5 or latest one in
Vim /home/kali/snehal/reengine/web/Dockerfile

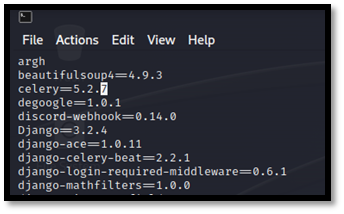
Now we need to check celery version and change it from 5.1.2 to 5.2.7 or latest one in
Vim /home/kali/snehal/reengine/web/requirements.txt
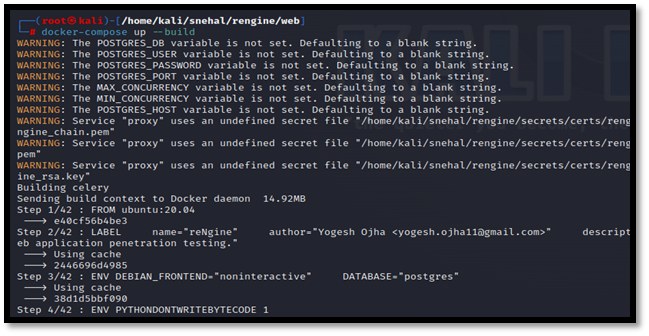
Now all we need to do is execute the following command and it will automatically install all the necessary servers and files and build a vulnerability scanner without much effort.
docker-compose up –build or ./install.sh
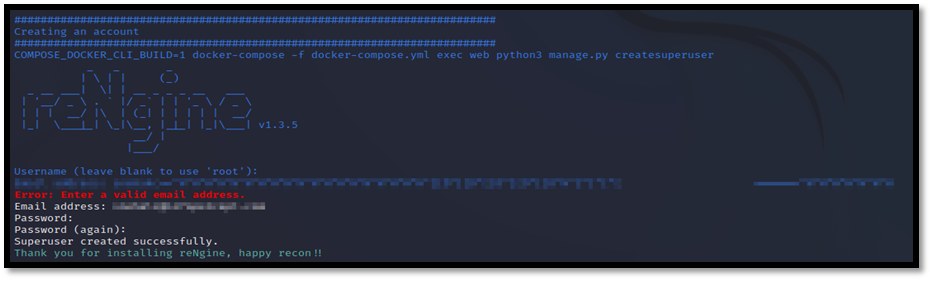
This may take some time but after the process is complete, add username, email, and password to create user.
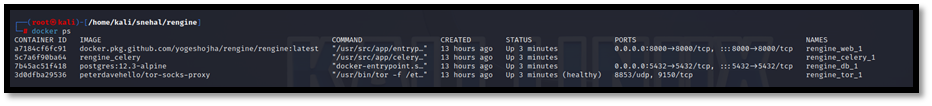
We can check the location of our web server by the ps command.
docker ps
Now check https://127.0.0.1
Here is the Initial Dashboard
Let’s perform our first scan!
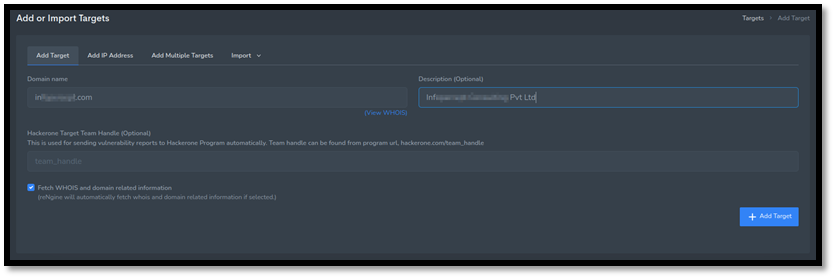
Step 1: Create a target
Go to the targets tab and add a new target. Enter the domain name and if wanted, a description.
That will get you to the following view, where you can see that we’ve never scanned this target before. Let’s change that!

Step 2: Perform your first scan
Click the lightning icon next to your target to initiate a scan. You will be redirected to a page where you can select the engine to be run on your target. In this case, I would like to perform a subdomain scan, so I select that one.

I have to cover every feature in depth so this one is really, really cool. Is a subdomain out of scope? Don’t worry, just list them here and they will not be scanned!

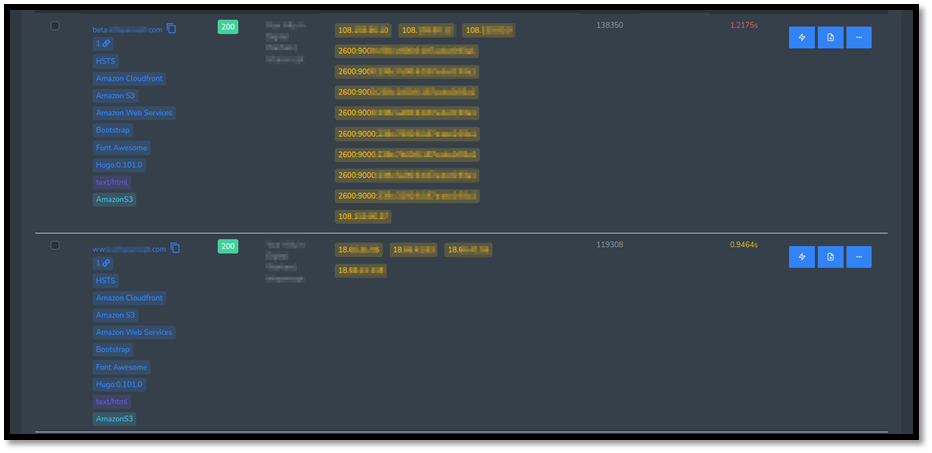
Step 3: Assessing the results
Once your scan is finished, you can view all the results.
Let’s cover some more features that ReNgine has to offer
• Reconnaissance: Subdomain Discovery, IP and Open Ports Identification, Endpoints Discovery, Directory and Files Fuzzing, Screenshot Collection, Nuclei-based Vulnerability Scan, WHOIS Identification, WAF Detection, etc.
• Capability for Parallel Scans and Subscans • Extremely customizable YAML-based Scan Engines.
• Perform advanced query lookup using natural language similar and, or, not operations. Recon Data visualisation. OSINT capabilities (meta info gathering, employee gathering, email address with an option to look password in the leaked database, - dorks, etc.). Customizable alerts/notifications on Slack, Discord, and Telegram.
• To-Dos and Recon Notes.
• Periodic Scans (run reconnaissance every X minutes/-hours/days/week) and Clocked Scans (run reconnaissance precisely at X Hours and Y Minutes).
• Filtered Screenshot Gallery and Proxy Support.
• Effective filtering of recon data with autosuggestions.
• Recon Data updates, discovers new/removed endpoints/subdomains.
• Add other tools from GitHub/Go • Interoperable with other tools, Import/Export Subdomains/Endpoints • Tag targets into the Organization • Detect Interesting Subdomains • Custom GF patterns and custom Nuclei Templates • Modify tool-related configuration files (Nuclei, Subfinder, Naabu, etc).
• Report Generation • Import Targets through IP and/or CIDRs.
• Toolbox: This package includes the most popular utilities, including whois lookup, CMS detector, CVE lookup, etc.
• Identifying relevant domains and TLDs for targets.
• Discover information that may be used to take action, such as the Most Common Vulnerability, Most Common CVE ID, Most Vulnerable Target/Subdomain, etc.
And so, so much more
For a more extensive explanation check out the GitHub repository at https://github.com/yogeshojha/rengine
Last but not least, reNgine provides a straightforward yet intuitive user interface that enables users to prepare and execute reconnaissance scans, monitor and analyse the acquired data, and create in-depth reports. Because of this, both seasoned security experts and people who are just learning about web application reconnaissance may use reNgine.
reNgine is a strong and flexible open-source tool for web application reconnaissance.. It offers a compelling alternative to conventional reconnaissance tools and may even be a better alternative for currently available commercial tools due to its emphasis on streamlining the recon process via engines, recon data correlation, continuous monitoring, database-backed recon data, and a simple yet intuitive user interface. ReNgine is unquestionably worthwhile investigating if you’re seeking a more effective and efficient approach to do web application reconnaissance.
In today’s digital age, application security has become a critical concern for businesses of all sizes. As applications become more complex, and the amount of sensitive data they handle increases, the risk of cyber-attacks and data breaches also rises. To counter these threats, many organizations are turning to application security platforms like Grepmarx to provide comprehensive protection for their applications.
Grepmarx is a web application providing a single platform to quickly understand, analyze and identify vulnerabilities in possibly large and unknown code bases.
https://github.com/Orange-Cyberdefense/grepmarx.git
Grepmarx is an application security platform that offers a range of tools and features to help businesses identify and mitigate security vulnerabilities in their applications. It uses machine learning algorithms and other advanced techniques to analyze code and detect potential security flaws, enabling organizations to identify and address vulnerabilities before they can be exploited.
One of the key features of Grepmarx, is its ability to perform dynamic analysis of applications in real-time. This means that it can detect vulnerabilities as they occur, even in applications that are actively being used by customers or employees. By constantly monitoring for security issues, Grepmarx can help organizations stay one step ahead of potential attackers.
Another important feature of Grepmarx is its support for multiple programming languages and frameworks. This means that it can be used to analyze and secure applications built on a variety of platforms, including Java, .NET, and Ruby on Rails, among others. This flexibility makes it a powerful tool for organizations with diverse application portfolios.
In addition to its dynamic analysis capabilities, Grepmarx also offers a range of static analysis tools that can be used to identify potential security issues before an application is even deployed. By analyzing source code and identifying potential issues early on, Grepmarx can help developers and security teams address vulnerabilities at the code level, reducing the risk of exploitation down the line.
Another key feature of Grepmarx is its reporting and analytics capabilities. The platform provides detailed reports on the security posture of an organization’s applications, including information on vulnerabilities, remediation efforts, and other key metrics. This information can be used to help prioritize security efforts and allocate resources more effectively.
Grepmarx is provided with a configuration to be executed in Docker and Gunicorn.
Requirements
• Linux
• Gunicorn
• Docker
Installation is quite simple. First, we must check whether docker -composer is installed on the system, and docker daemon is running. The application can then be easily executed in a docker container.
1. Get the code
$ git clone https://github.com/Orange-Cyberdefense/grepmarx.git $ cd grepmarx
2. Start the app in Docker
$ sudo docker-compose pull && sudo docker-compose build && sudo docker-compose up -d
Visit http://localhost:5000 in your browser. The app should be up & running.
Note: a default user account is created on first launch (user=admin / password=admin). Change the default password immediately.
Gunicorn ‘Green Unicorn’ is a Python WSGI HTTP Server for UNIX. A supervisor configuration file is provided to start it along with the required Celery worker (used for security scans queuing).
1. Install using pip:
$ pip install gunicorn supervisor
2. Start the app using gunicorn binary:
$ supervisord -c supervisord.conf
Visit http://localhost:8001 in your browser. The app should be up & running.
Note: a default user account is created on first launch (user=admin / password=admin). Change the default password immediately.
Step 1:
Step 2:
It will take hardly 10-15 minutes to install all dependences in docker container.
Step 1: Access Web interface
Access the web interface at http://127.0.0.1:5000
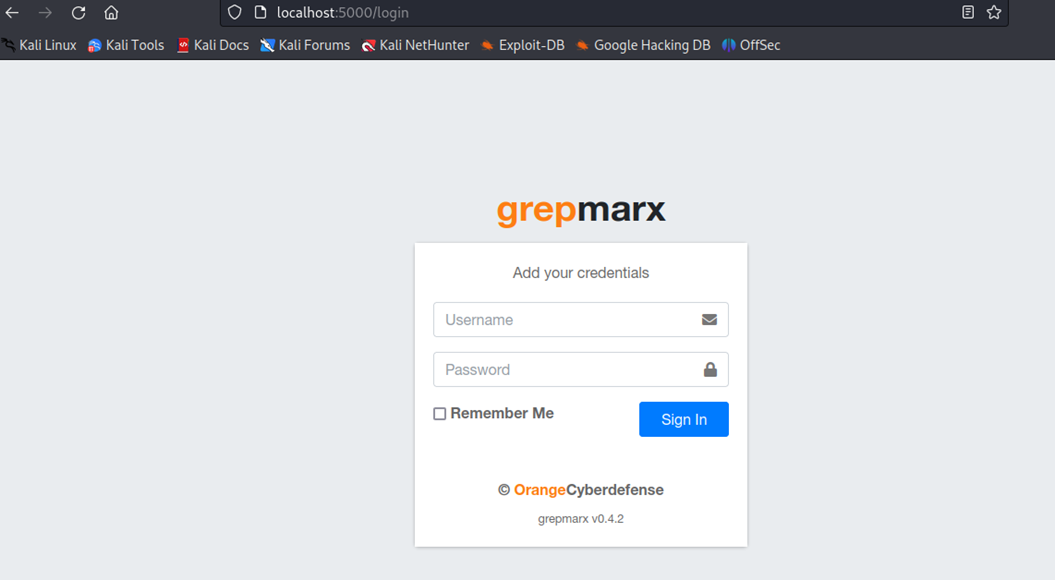
Username – admin
Password – admin
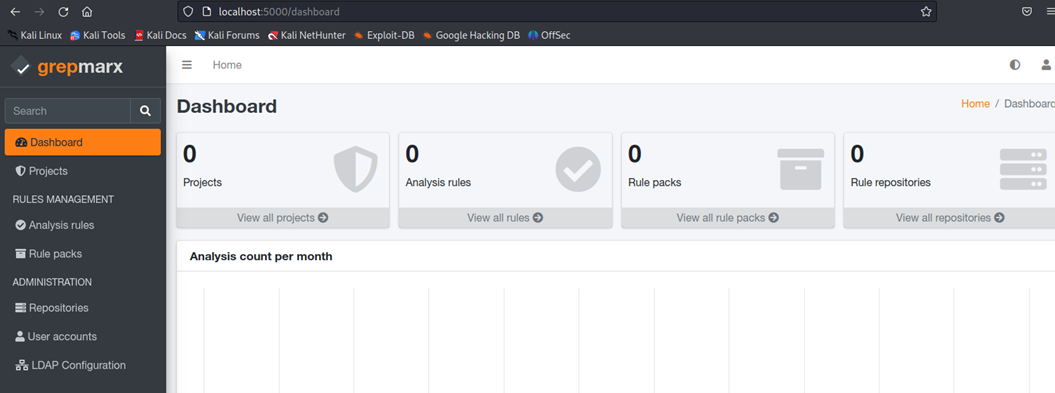
Step 2: Perform your first scan
Click the lightning icon next to your target to initiate a scan. You will be redirected to a page where you can select the engine to be run on your target. In this case, I would like to perform a subdomain scan, so I select that one.
I must cover every feature in depth so this one is really,cool. Is a subdomain out of scope? Don’t worry, just list them here and they will not be scanned!

Step 3: Launch the Scanner
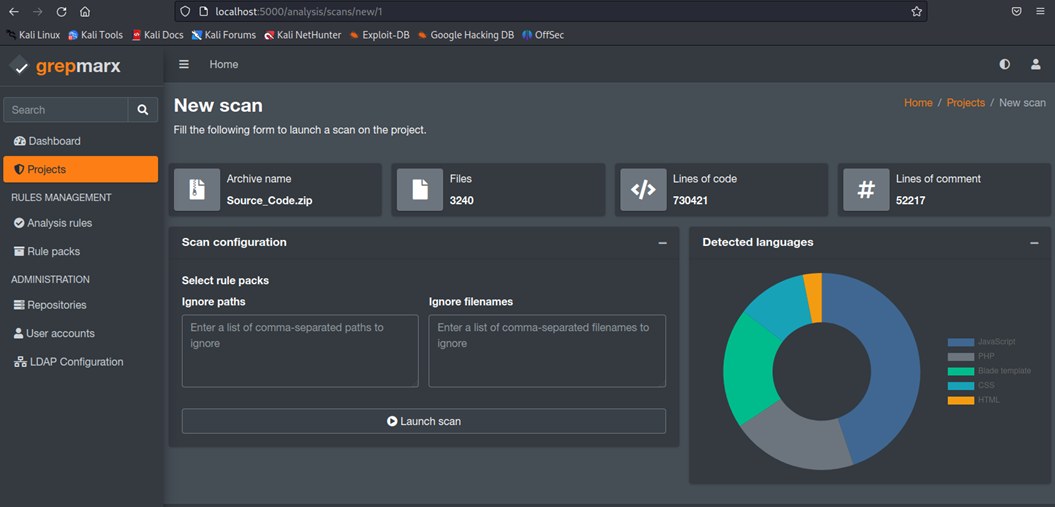
Once your scan is finished, you can view all the results
Let’s cover some more features that Grepmarx has to offer
SAST (Static Analysis Security Testing) capabilities:
• Multiple languages support: C/C++, C#, Go, HTML, Java, Kotlin, JavaScript, TypeScript, OCaml, PHP, Python, Ruby, Bash, Rust, Scala, Solidity, Terraform, Swift.
• Multiple frameworks support: Spring, Laravel, Symfony, Django, Flask, Node.js, jQuery, Express, Angular…
• 1600+ existing analysis rules.
• Easily extend analysis rules using Semgrep syntax: https://semgrep.dev/editor
• Manage rules in rule packs to tailor code scanning.
SCA (Software Composition Analysis) capabilities:
• Multiple package-dependency formats support: NPM, Maven, Gradle, Composer, pip, Gopkg, Gem, Cargo, NuPkg, CSProj, PubSpec, Cabal, Mix, Conan, Clojure, Docker, GitHub Actions, Jenkins HPI, Kubernetes.
• SBOM (Software Bill-of-Materials) generation (CycloneDX compliant).
Extra
• Analysis workbench designed to efficiently browse scan results
• Scan code that doesn’t compile
• Comprehensive LOC (Lines of Code) counter
• Inspector: automatic application features discovery
• … and a Dark Mode
And so, so much more For a more extensive explanation check out the GitHub repository at https://github.com/Orange-Cyberdefense/grepmarx.git
Finally, it’s worth noting that Grepmarx is designed to be easy to use and integrate into existing development workflows. The platform provides APIs and integrations with popular development tools like Jira and Jenkins, making it easy for developers and security teams to incorporate security testing into their existing processes.
In conclusion, Grepmarx is a powerful application security platform that offers a range of features and tools to help organizations identify and mitigate security vulnerabilities in their applications. With its support for multiple programming languages and frameworks, dynamic and static analysis capabilities, and robust reporting and analytics, Grepmarx is a valuable tool for any organization looking to enhance its application security posture.
Discover complete cybersecurity expertise you can trust and prove you made the right choice!
